[Android逆向]复现记录frida dump dex并hook
前言
看到先知师傅一篇android逆向,感觉很有趣,就复现了下,做下记录
环境
frida-server
Jeb 3.17
mumu模拟器
某apk
Frida-tools
FRIDA-DEXDump: https://github.com/hluwa/FRIDA-DEXDump
Root 过的android手机
frida dex dump
环境安装
FRIDA-DEXDump:https://github.com/frida/frida/releases
选择frida-server-12.8.20-android-x86.xz
导入mumu模拟器中,并开启
adb push frida-server-12.8.20-android-x86 /data/local/tmp
chmod 777 frida-server-12.8.20-android-x86
./frida-server-12.8.20-android-x86root过的android手机上运行app,执行FRIDA-DEXDump,拿到dex(发现在mumu模拟器上dump到的dex不完整)
python3 main.py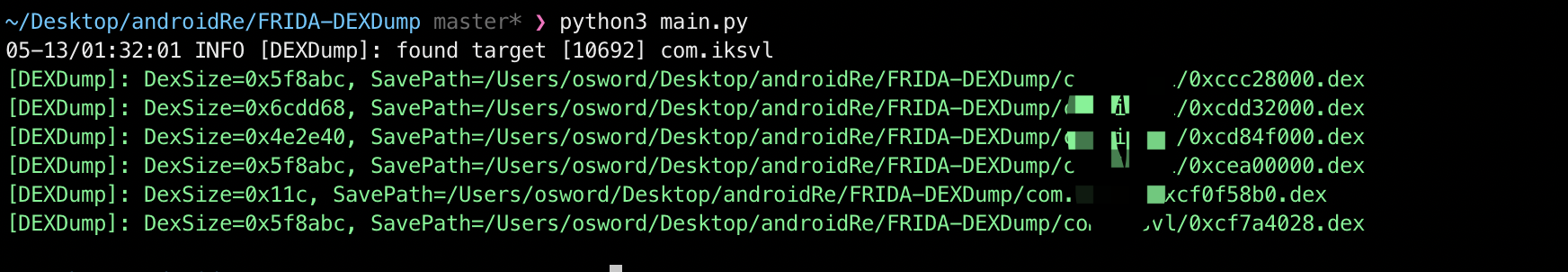
jeb 逆向分析
使用jeb 打开dex文件
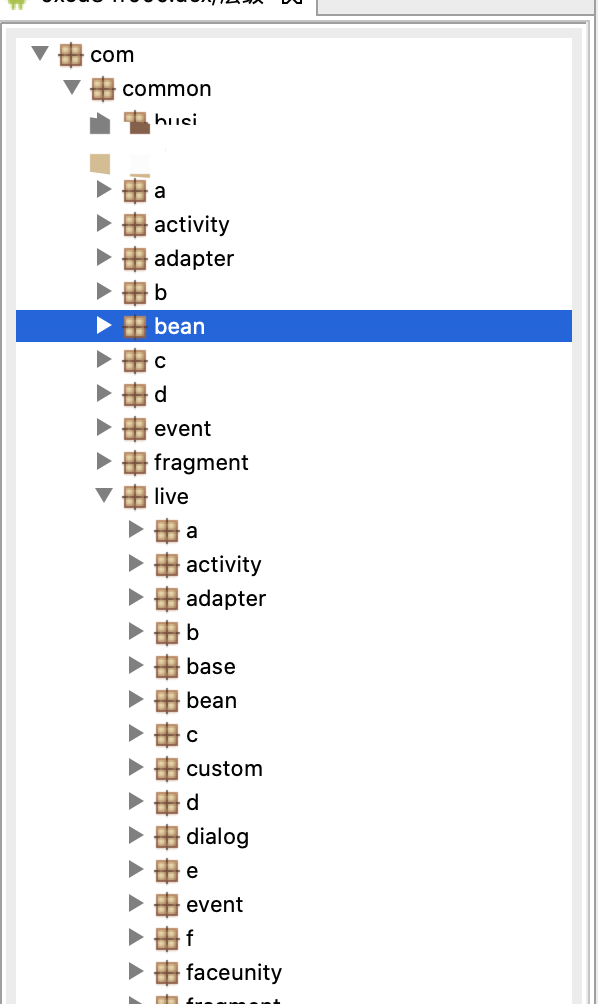
跟进com.xxx.bean.UserBean 看用户模块
isVV为控制vip权限处,hook这里就ok了

frida hook
Hook.js
if(Java.available) {
console.log('ok111');
Java.perform(function(){
var application = Java.use("android.app.Application");
console.log('ok222');
application.attach.overload('android.content.Context').implementation = function(context) {
console.log('ok333');
var result = this.attach(context); // 先执行原来的attach方法
var classloader = context.getClassLoader(); // 获取classloader
Java.classFactory.loader = classloader;
console.log('ok444');
var userinfo = Java.classFactory.use("com.xxxx.bean.UserBean");
console.log("user: " + userinfo);
userinfo.isVV.implementation = function(){
return true;
}
userinfo.getVVLevel.implementation = function(){
return "9";
}
return result;
}
});
}shell1设置端口转发
# shell1
adb forward tcp:1234 tcp:1234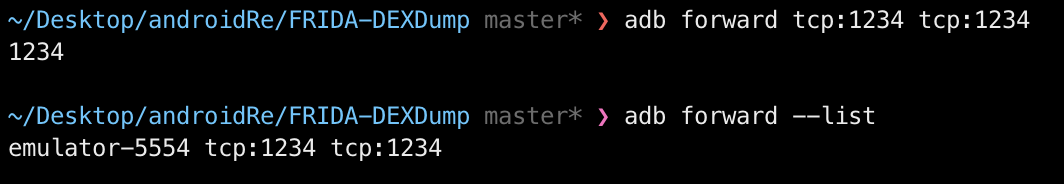
Shell2开启监听,换到mumu模拟器
# shell2
adb kill-server & adb start-server & adb shell
frida-server-12.8.20-android-x86 -l 0.0.0.0:1234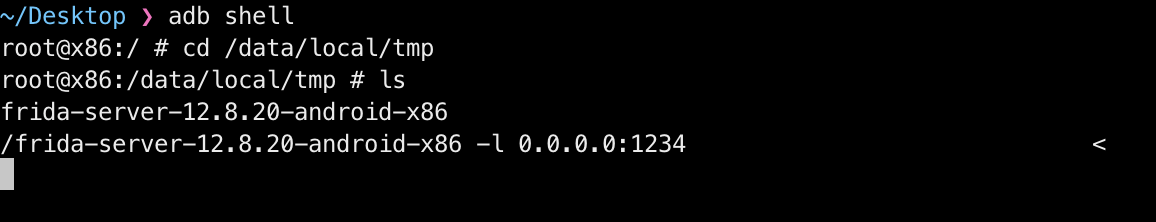
shell1开始hook
frida -H 127.0.0.1:1234 -f com.iksvl -l hook.js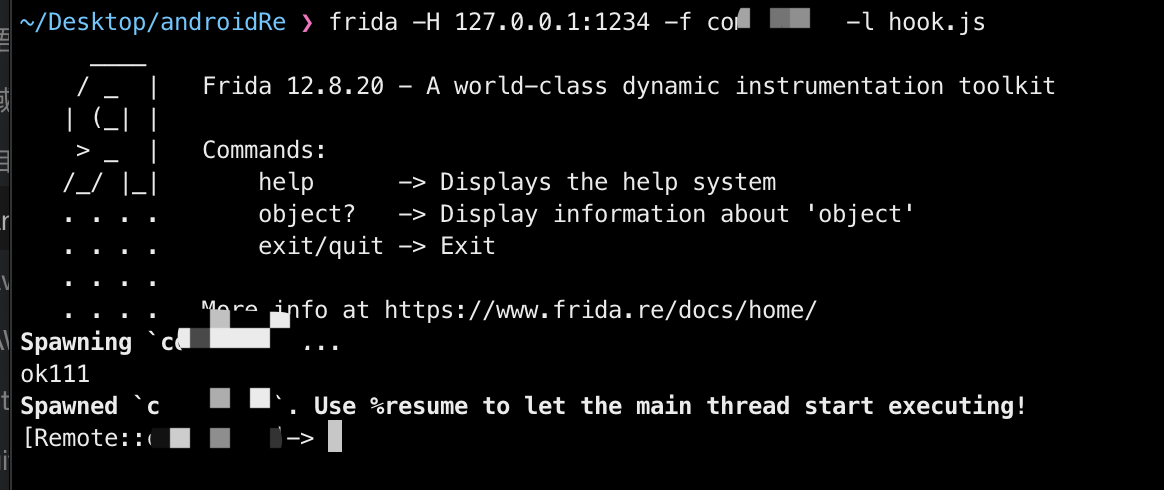
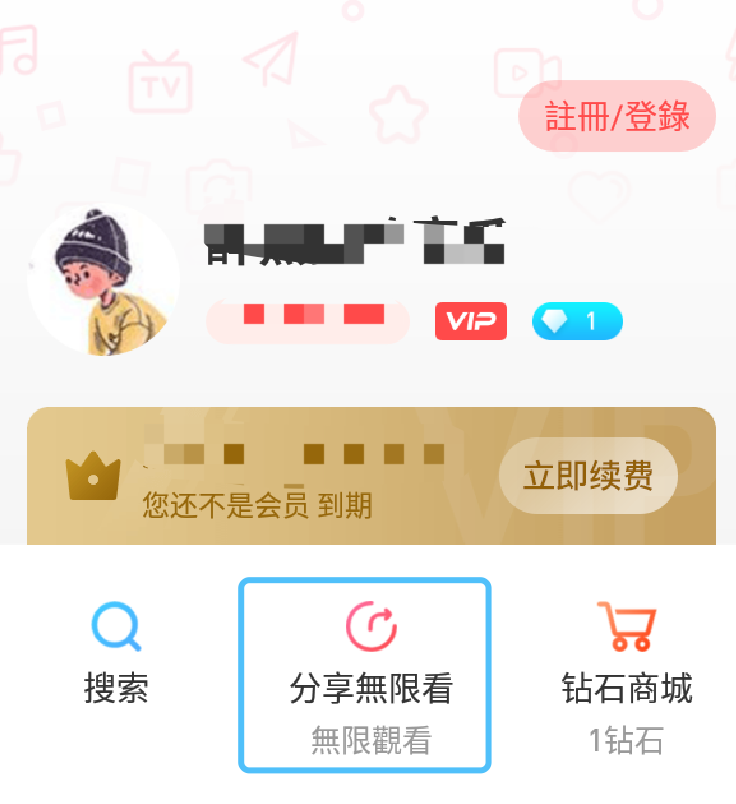
%resume开启android应用,获得会员权限
本来想hook改掉钻石数,没成功(哈哈哈)
参考链接
本博客所有文章除特别声明外,均采用 CC BY-SA 4.0 协议 ,转载请注明出处!